With data breaches on the rise and regulations tightening across industries, protecting sensitive information has never been more critical. In 2023 alone, organizations faced a staggering 78% increase in data compromises — a clear signal that traditional security methods are struggling to keep up.
Encryption has long been the go-to solution, but as data moves faster and across more systems — databases, APIs, streaming pipelines, and third-party platforms — encryption alone often isn't enough. This is where data tokenization comes in.
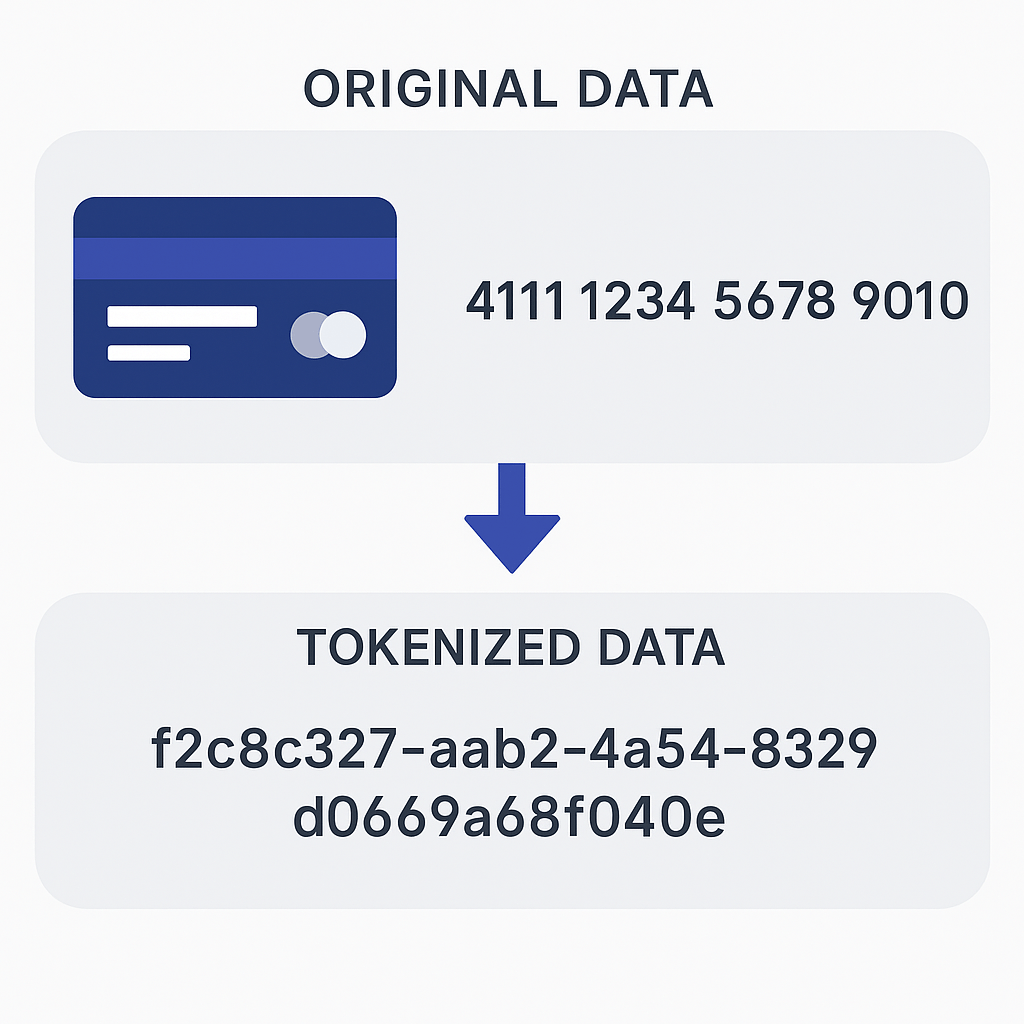
Data tokenization replaces sensitive information like credit card numbers, medical records, or personal identifiers with non-sensitive placeholders called tokens. These tokens retain enough structure to be useful for analytics and operations but are meaningless if intercepted, offering both security and flexibility.
In this guide, we'll break down how tokenization works, why it's so effective, and where it's being used today — from e-commerce platforms and hospitals to AI-powered applications. You'll also learn how tokenization fits into real-time data pipelines and how platforms like Estuary support secure access and movement of sensitive data through token-based authentication.
Let’s start by understanding the basics.
What is Data Tokenization?
Data tokenization is a method of protecting sensitive information by replacing it with a non-sensitive equivalent — called a token — that has no exploitable meaning or value outside of its intended system. Unlike encryption, which transforms data into unreadable formats using keys, tokenization substitutes the data entirely, storing the real value separately in a secure token vault.
Think of it this way: if sensitive data is a house key, encryption hides it in a locked box. Tokenization, on the other hand, gives you a fake key that won’t open anything — unless you're authorized to retrieve the real one from a separate vault.
Example
Let’s say your system captures a user’s credit card number:
4111 1111 1111 1111
With tokenization, this number might be replaced with:
tok_c4a9f8b3-2104-439b-926f-f94b1fe55c2f
The token is stored and used across systems — for analytics, transaction routing, or logging — but the original card number is never exposed. If an attacker gains access to the token, it’s useless without access to the secure vault where the mapping is stored.
Key Characteristics of Tokenization
- Irreversible without a token vault: Unlike encrypted data, tokens can’t be converted back without secure access to the original mapping.
- Format-preserving (optional): Tokens can be structured to match the format of the original data (e.g., last 4 digits of a credit card) for usability.
- Minimal compliance exposure: Since tokenized data isn't considered "real" sensitive data, it may reduce regulatory burden.
In the next section, we’ll walk through how the tokenization process works — from identifying sensitive fields to securely replacing and managing data in production environments.
How Does Data Tokenization Work?
The tokenization process follows a structured flow designed to protect sensitive data while allowing business operations to continue as normal. It centers around replacing sensitive values with tokens and storing the original data in a secure token vault, often separate from the systems that process or analyze data.
Here’s a breakdown of how tokenization works step-by-step:
Step 1: Identify Sensitive Data
Before tokenization begins, the system must recognize what data needs to be protected. This typically includes:
- Personally identifiable information (PII) — e.g., names, SSNs
- Payment details — e.g., credit card numbers
- Healthcare records — e.g., patient IDs, prescriptions
- Financial data — e.g., account balances, transactions
Step 2: Generate Tokens
Once identified, each piece of sensitive data is replaced with a token, usually a randomly generated string with no intrinsic value.
Example:
Original SSN → 123-45-6789
Token → tok_2987de93-44aa-4e3e-9c35-55d9a54b2c70
Tokens can optionally preserve format or partial data for usability (e.g., show last 4 digits of a card number).
Step 3: Map Tokens to Original Data (Vault Storage)
A secure token vault stores the mapping between each token and its corresponding original value. This vault is:
- Encrypted
- Access-controlled
- Often hosted separately from other infrastructure
This separation ensures that even if a system using the tokenized data is breached, the original sensitive data remains protected.
Step 4: Use Tokens in Downstream Systems
Now, the tokenized data can be safely used in:
- Analytics and reporting
- Logging
- Application workflows
- Data sharing between departments or partners
Because tokens don't contain usable sensitive data, they drastically reduce exposure risk, making them safe for use in broader environments.
Step 5: Detokenize (When Necessary)
In some cases (e.g., processing a payment or verifying an identity), systems may need to retrieve the original data. Only authorized systems can detokenize the data by querying the secure vault.
Access controls, logging, and auditing are essential here to prevent misuse.
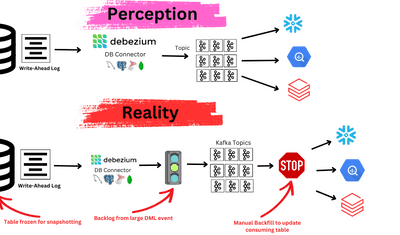
Real-Time Tokenization in Pipelines
In traditional systems, tokenization happens in batch jobs or at the storage layer. But in modern architectures — especially real-time pipelines — tokenization needs to happen in motion.
For example:
- A streaming pipeline that captures user events from Postgres or Kafka can apply tokenization as part of an in-flight transformation, ensuring sensitive fields are never stored or exposed.
That’s why the next section explores how tokenization differs from encryption, and why it's increasingly important for secure, flexible data operations.
Data Tokenization vs. Encryption
Both tokenization and encryption are data protection techniques, but they solve different problems and are built on fundamentally different principles. Understanding when and how to use each is key to designing secure and compliant data systems.
Let’s break it down:
Encryption: Locking Data with a Key
Encryption transforms sensitive data into an unreadable format using cryptographic algorithms and a secret key. The original data can only be recovered (decrypted) with that key.
Example:
Credit card 4111 1111 1111 1111 → Encrypted as f84e2d6f4a57a1a...
Decryption requires the same key or a corresponding private key (depending on the method).
Pros:
- Reversible
- Ideal for protecting data in transit or at rest
- Widely supported by databases, storage systems, APIs
Cons:
- Still exposes data during use (e.g., once decrypted)
- Managing keys is complex and risky
- Breach of key = breach of all encrypted data
Tokenization: Replacing Data with Placeholders
Tokenization replaces data with meaningless tokens, with no mathematical relationship to the original values. The mapping is stored separately in a secure vault.
Example:
Credit card 4111 1111 1111 1111 → Tokenized as tok_92f3b7b1...
Pros:
- Tokens are useless if intercepted
- No decryption risk — no key to steal
- Often exempt from full compliance audits (e.g., PCI, HIPAA)
Cons:
- Requires secure vault infrastructure
- Limited use for some analytical or transactional scenarios
- Not a fit for data that needs reversible access across many systems
Key Differences: Tokenization vs Encryption
Feature | Tokenization | Encryption |
| Data Relationship | No relationship to original data | Mathematically related to original data |
| Reversibility | Only via token vault | Yes, with decryption key |
| Format-Preserving | Optional | Typically not (but can be configured) |
| Security Scope | Protects data at rest and in use | Protects data in transit and at rest |
| Breach Exposure | Tokens are useless if stolen | Encrypted data can be decrypted if key leaks |
| Compliance Scope | May reduce audit scope | Usually still subject to audit |
Which Should You Use?
- Use Encryption when: You need to store or transmit sensitive data securely, especially when it must be readable on the other end.
- Use Tokenization when: You want to minimize exposure and eliminate sensitive data from your stack entirely, especially in real-time analytics or customer-facing systems.
In practice, many organizations use both: encrypting data at rest, and tokenizing it for internal processing, data sharing, and privacy preservation.
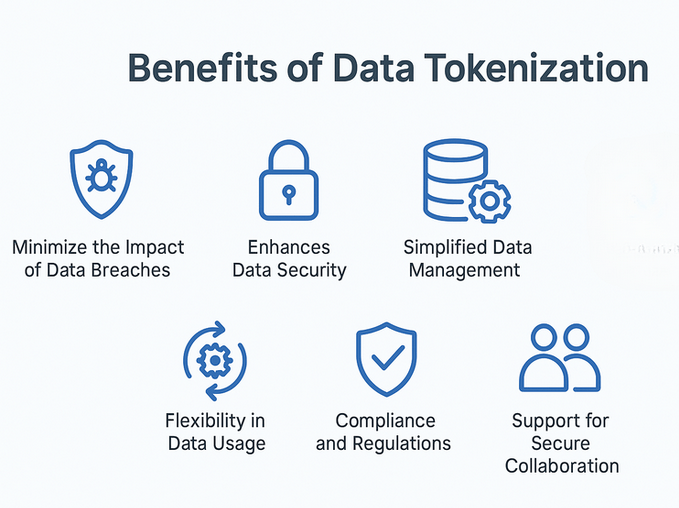
Benefits of Data Tokenization
Data tokenization isn’t just a security tactic — it’s a strategic enabler for businesses that want to reduce risk, simplify compliance, and work with sensitive data more confidently across systems and teams.
Let’s break down the key benefits:
1. Minimizes the Impact of Data Breaches
Tokenized data holds no exploitable value. If attackers gain access to a system containing tokens (but not the secure vault), they can’t reverse-engineer the original data.
Example:
A stolen token like tok_8a1f3cdd... doesn’t reveal anything about a credit card or social security number, dramatically limiting breach fallout.
2. Enhances Data Security in Use
Encryption protects data in storage or during transmission — but it’s decrypted during use, introducing risk. Tokenized data, on the other hand, can stay protected even during processing.
Use case:
A customer service dashboard can display anonymized tokens rather than exposing full PII, improving internal security posture.
3. Simplifies Data Management
Tokenization separates sensitive data from operational data, making it easier to:
- Audit and manage sensitive fields
- Minimize scope of access control
- Enforce the principle of least privilege
It also reduces dependencies between departments needing access to “some” data but not all of it.
4. Enables Secure Data Sharing
Tokens allow companies to share meaningful representations of data (e.g., usage trends, behaviors, demographics) without exposing real identities or financial information.
Example:
Marketing, support, and analytics teams can all access customer interaction logs without ever touching raw personal data.
5. Reduces Compliance Scope
Many regulations (PCI DSS, HIPAA, GDPR) treat tokenized data differently than raw data. If your systems only handle tokens — not the original PII — they may be exempt from full audit requirements.
- Less time on compliance
- Fewer security obligations for internal tools
- Faster time to deploy analytics or data products
6. Supports Data Privacy by Design
Tokenization is a foundational technique for privacy-preserving architectures, where data minimization, masking, and access control are enforced by default.
This aligns with modern frameworks like:
- GDPR’s data minimization principle
- HIPAA’s de-identification strategies
- Zero-trust security models
Real-World Use Cases of Data Tokenization
Tokenization is more than a technical concept — it’s a practical solution to real problems across industries that deal with high volumes of sensitive information. From credit card processing to AI pipelines, tokenization helps reduce risk without slowing down operations.
Here are some of the most impactful use cases:
1. Financial Services and Payment Processing
Challenge: Storing and transmitting credit card details is risky and heavily regulated under PCI DSS.
Solution: Tokenize payment information during checkout so only tokens are stored and used for billing or refunds.
Example: When a customer saves a card for recurring billing, the payment processor stores the actual card number in a vault, while the merchant stores a token like tok_cc9a….
Impact: Reduced PCI audit scope, safer transactions, and fewer compliance headaches.
2. Healthcare and Patient Records
Challenge: Electronic Health Records (EHR) contain highly sensitive patient data and must comply with HIPAA.
Solution: Tokenize identifiers such as patient ID, insurance numbers, and diagnoses when sharing or analyzing medical data.
Example: A research team can analyze patient treatment outcomes without seeing names or full records — only tokenized identifiers.
Impact: Protected patient privacy, compliant collaboration, and accelerated medical research.
3. Retail & E-Commerce Analytics
Challenge: Retailers want to understand customer behavior without exposing identity or violating privacy laws.
Solution: Tokenize customer IDs, emails, or phone numbers before data reaches analytics platforms.
Example: A company can evaluate the performance of loyalty programs using tokenized data, segmented by token rather than personal info.
Impact: Privacy-preserving personalization, GDPR compliance, and secure cross-department data sharing.
4. Natural Language Processing (NLP) and AI Pipelines
Challenge: Text data often contains names, addresses, or other identifiers that shouldn’t be used during training or inference.
Solution: Tokenize or mask these entities before passing text into AI models.
Example: Before training a chatbot on customer service transcripts, you tokenize names ([NAME_001]) and addresses ([ADDRESS_015]).
Impact: Safer model training, compliance-friendly AI, and better handling of sensitive language.
5. API Security and Data Sharing
Challenge: APIs and third-party systems introduce risks when handling PII or financial data.
Solution: Tokenize data before sending it to external vendors or sharing across business units.
Example: A logistics provider shares shipment tracking data with partners, but customer names and addresses are tokenized before transmission.
Impact: Secure partner integrations, better control over data exposure, and modular system design.
In the next section, we’ll zoom in on real-time use cases and explore why traditional batch tokenization models are no longer enough in fast-moving data ecosystems.
Tokenization in Real-Time Pipelines: Why It Matters Now
Historically, tokenization was applied in batch jobs or during ETL workflows — long after data had been collected, stored, and sometimes even shared. But in today’s environment, that’s often too late.
As businesses adopt real-time analytics, event-driven architectures, and automated decision systems, tokenization needs to happen in motion, not just at rest.
Why Traditional Tokenization Falls Short
- It often happens after sensitive data has already passed through multiple systems.
- It’s batch-oriented, meaning delayed protection, especially in systems with high-velocity or continuous ingestion.
- It assumes that data is stored before being secured, increasing breach exposure and compliance risk.
Streaming Pipelines Change the Game
Modern data pipelines:
- Capture changes from operational databases using CDC (Change Data Capture)
- Stream events into data lakes, warehouses, or applications in real time
- Trigger transformations and machine learning models on the fly
In these environments, sensitive data can travel across connectors, brokers, cloud functions, and dashboards — often within seconds. Without real-time tokenization or protections at each stage, your systems are vulnerable.
Where Tokenization Fits in a Streaming Stack
You can apply tokenization:
- At the ingestion layer (e.g., as data enters from Postgres, MongoDB, or an API)
- During stream processing (e.g., in a SQL-based transformation tool)
- Before materialization (e.g., syncing data to Snowflake or ClickHouse with masked fields)
This allows you to:
- Maintain privacy and compliance while still enabling fast, usable data
- Share tokenized insights with downstream systems instantly
- Eliminate exposure windows between data capture and transformation
How It Works in Practice
Imagine a healthcare analytics platform streaming patient records from a MySQL database to a HIPAA-compliant analytics warehouse.
With traditional tokenization, sensitive data might already exist in storage, creating compliance and breach risks.
With real-time tokenization built into the pipeline, patient identifiers are replaced immediately as the data flows, never touching storage or being exposed downstream.
The Bottom Line:
Tokenization in real-time pipelines isn’t just a “nice-to-have.” It’s essential for:
- Complying with data protection laws (e.g., HIPAA, GDPR, PCI DSS)
- Preventing breach impact in high-throughput systems
- Enabling secure, responsive business operations — without delays
In the next section, we’ll show how Estuary helps you secure access to real-time pipelines using token-based authentication, aligning with the same principles that make data tokenization effective.
How Estuary Secures Real-Time Pipelines Using Token-Based Access
While data tokenization focuses on replacing sensitive values during processing, a lesser-discussed — but equally important — layer of protection lies in who can access the pipeline in the first place. Estuary addresses this through secure, token-based authentication that aligns with the principle of least privilege — a core tenet of modern data security.
Estuary enables organizations to build real-time pipelines that not only move data instantly, but also safeguard how that data is accessed, controlled, and orchestrated across development environments.
Built-In Access Token Management
Estuary’s CLI (flowctl) and programmatic API access are protected using personal and service-level refresh tokens.
- Each token is scoped to a specific identity or purpose (e.g., “marketing-pipeline”, “dbt-trigger-bot”)
- Tokens can be:
- Labeled for visibility
- Expired on demand
- Rotated regularly
This approach gives teams fine-grained control over who (or what service) can trigger builds, deploy flows, or read/write configurations.
Aligned with the Principle of Least Privilege
Rather than granting broad access to users or systems, Estuary enables scoped access tokens for each automated task or connector.
Example: You can generate a refresh token that only authorizes syncing data from Shopify to ClickHouse, but can’t modify other parts of your pipeline or access unrelated collections.
This enforces the least privilege model across both human and machine users, reducing exposure, isolating risk, and improving auditability.
flowctl: Secure, Tokenized CLI for Automation
The Estuary CLI (flowctl) is ideal for engineers who want to script or automate real-time pipelines, without compromising on security.
- Authenticate once with a short-lived token tied to your identity
- No need to store passwords or persistent secrets
- Ideal for CI/CD pipelines, remote environments, and controlled development setups
This ensures that only authorized and verified processes interact with your flows, connectors, and collections.
Secure Deployment and Infrastructure Controls
Estuary also supports enterprise-grade deployment options:
- Private Cloud & BYOC (Bring Your Own Cloud)
- VPC Peering & PrivateLink
- Encrypted data in transit and at rest
Even though Estuary doesn’t perform data tokenization in the cryptographic sense, it ensures your tokenized data:
- Moves securely between systems,
- Is accessed only by trusted agents, and
- Stays protected across the pipeline lifecycle.
Whether you're processing customer PII, financial data, or clinical records, Estuary helps you secure every layer of the pipeline — from access to delivery — using token-based authentication and cloud-native isolation.
Conclusion
In a world where data breaches, compliance risks, and privacy regulations are growing more intense by the year, data tokenization is no longer optional — it’s essential.
Whether you’re processing credit card payments, managing patient records, analyzing user behavior, or building AI models, tokenization gives you a way to retain value while eliminating risk. It protects sensitive data without blocking teams from using it, enabling analytics, automation, and collaboration at scale.
But as pipelines become faster and more dynamic, traditional batch tokenization isn’t enough. Organizations need tools that support real-time data protection, secure programmatic access, and automation-friendly workflows.
That’s where Estuary shines.
While not a payload tokenization engine, Estuary:
- Enables real-time movement of tokenized data across systems
- Enforces token-based access controls via its CLI and API
- Supports secure, automated data workflows aligned with the principle of least privilege
- Fits seamlessly into privacy-first architectures — from CDC to dashboards to transformation jobs
Whether you’re modernizing your data stack or securing high-sensitivity workloads, tokenization and real-time sync go hand in hand. Estuary helps you do both — with speed, scale, and security.
Ready to Secure Your Pipelines?
Explore how Estuary enables secure, real-time data movement with token-based authentication, private deployments, and powerful CDC integrations — all without writing complex code. Get Started with Estuary
FAQs
Is tokenized data considered personal data?
Is data tokenization reversible?

About the author
Team Estuary is a group of engineers, product experts, and data strategists building the future of real-time and batch data integration. We write to share technical insights, industry trends, and practical guides.