Modern organizations face an ever-growing landscape of regulatory requirements (GDPR, HIPAA, SOX, PCI-DSS, and many others) each with data integrity, auditability, and historical retention mandates. One often-overlooked enabler of compliance? Change Data Capture (CDC).
At Estuary, we’ve seen firsthand how CDC isn’t just for real-time analytics or application syncing, it's a linchpin for regulatory compliance. In this article, we’ll explore how CDC helps organizations retain historical changes in data for auditability and transparency, and how platforms like Estuary Flow make it easier than ever to implement.
Why Historical Data Matters for Compliance
Many compliance frameworks require you to track who changed what, when, and how, sometimes with extreme granularity. Here's why retaining historical data changes is essential:
- Auditability: Auditors need complete visibility into data changes, including deleted or overwritten records.
- Data provenance: Regulators often require an entire lineage of how a data point evolved.
- Forensics and breach analysis: If something goes wrong, you must be able to reconstruct events from historical data.
- Right to access and erasure (e.g., under GDPR): You must track changes to personal data and verify if data has been altered or deleted correctly.
These use cases all share a common requirement: a reliable log of data changes.
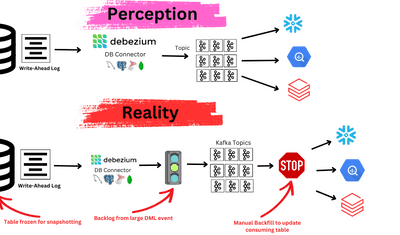
The Problem with Traditional Audit Trail Solutions
Before diving into the benefits of CDC, it’s worth examining how organizations typically try to build audit trails today—and why those methods often fall short, especially at scale or under scrutiny.
Manual Audit Tables in the Source Database
A common approach is to create a shadow “history” table that stores previous versions of records, populated via triggers or application logic.
While this can work in small systems, it comes with major drawbacks:
- High maintenance overhead: Schema changes must be mirrored manually. Triggers can break or behave unpredictably.
- Application coupling: The business logic responsible for writing to audit tables is embedded in the app, increasing complexity and risk.
- No coverage for deletes or failed writes: If an operation fails before the audit trail is written, or data is deleted without a proper trigger, the record disappears.
- Limited visibility into context: Many of these tables only store the "after" value, without a clear diff or user metadata.
Periodic Snapshots or Exports
Another approach is to export snapshots of the full dataset at regular intervals—daily, hourly, or even less frequently—and compare them to infer changes.
This method suffers from:
- Storage inefficiency: Snapshots duplicate large volumes of unchanged data.
- Lack of granularity: Mid-interval changes are missed. If a record changes twice in one hour, you’ll only see the end state.
- No real-time insight: These exports are inherently batch-oriented and delayed.
- Complex reconstruction: Piecing together the sequence of events from diffs between snapshots is error-prone and often requires custom tooling.
Log-Based Archival and Event Logging
Some teams try to log every user or system action to application-level logs or middleware systems. But:
- Logs are not data-aware: They lack schema structure and are difficult to query or audit programmatically.
- Retention is limited: Logs are often rotated out or stored separately from primary datasets.
- Correlation is hard: It’s difficult to trace a log event back to the precise change in the underlying data without complex joins and assumptions.
Why These Solutions Don’t Scale for Compliance
Regulations like GDPR, HIPAA, SOX, and others expect deterministic, verifiable, and immutable records of change—not best-effort approximations.
In practice, these traditional approaches:
- Fail under volume or schema evolution
- Are too fragile for high-trust environments
- Require significant developer effort to maintain
- Often miss key changes or create gaps in history
That’s why forward-thinking teams are turning to CDC pipelines as a foundation for durable, scalable, and queryable audit trails—backed by real-time change logs instead of approximations.
How Change Data Capture Works
Change Data Capture is a technique that captures changes—inserts, updates, and deletes—from source databases in real time. Rather than polling entire tables, CDC listens to the underlying transaction logs (e.g., MySQL binlog, PostgreSQL WAL) to efficiently stream changes as they happen.
CDC records each change with key metadata such as:
- Timestamp of change
- Operation type (INSERT, UPDATE, DELETE)
- Before and after values
- Primary key or identifying information
This structure creates a powerful chronological record of data evolution.
Using CDC for Compliance: Core Benefits
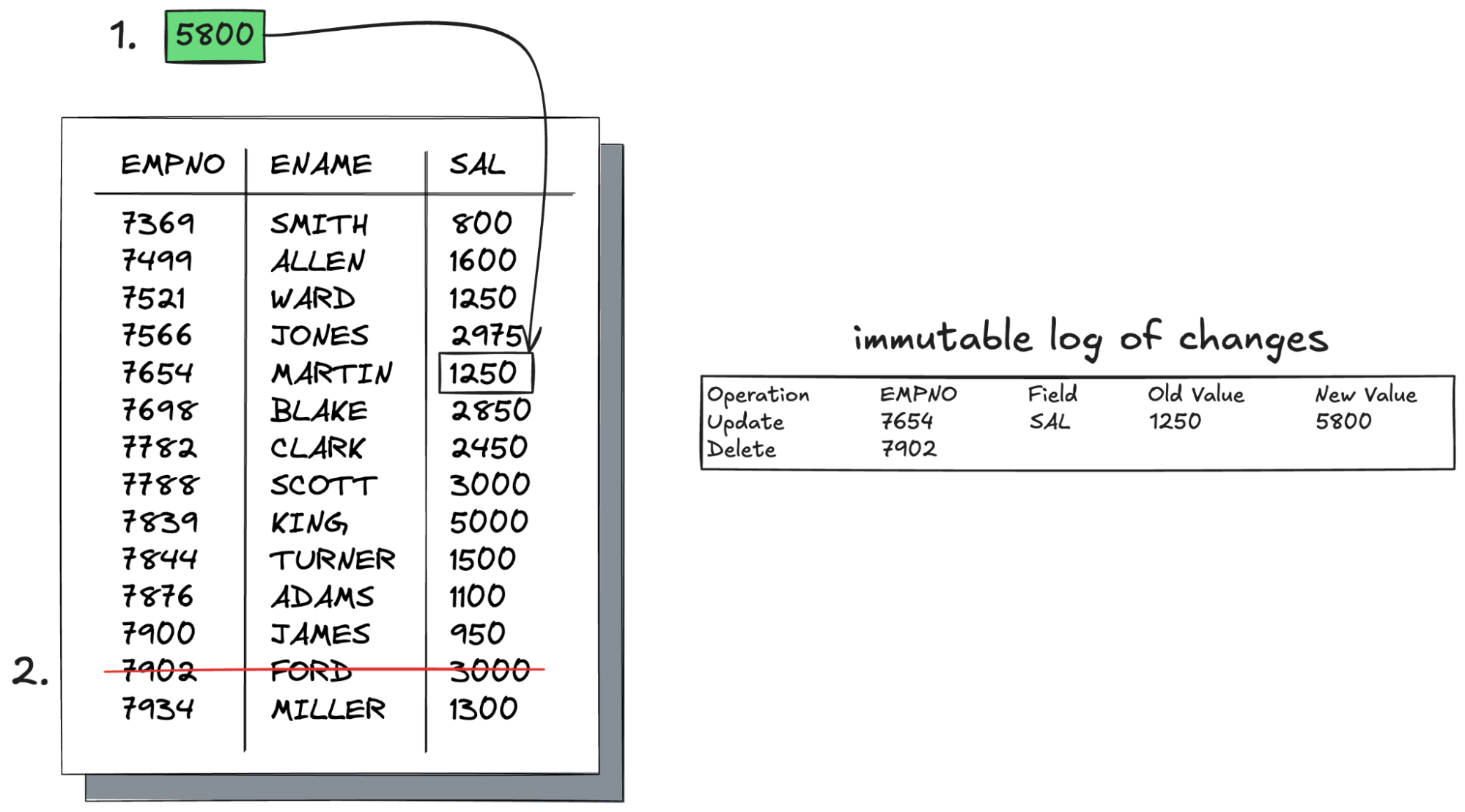
1. Immutable Audit Trails
You can retain a complete, immutable history of every change by writing CDC streams to an append-only log, such as an Apache Iceberg table or object storage. This fulfills the common requirement to demonstrate a complete audit trail for critical data.
2. Time Travel and Snapshots
CDC enables time travel across data states, letting you recreate how a record looked at any point in time. This is invaluable when:
- An auditor asks, “What did the record look like last March?”
- You need to verify whether a correction was made retroactively.
- You need to provide a legally verifiable version of historical truth.
3. Retention and Archival Policies
CDC data can be configured to support custom retention policies. For example, you might store 7 years of CDC logs for financial records per SOX, while only keeping 90 days for marketing data.
Using a platform like Estuary Flow, you can write CDC events to tiered storage systems (like S3, GCS, or Azure Blob) with lifecycle policies, balancing compliance with cost-efficiency.
4. Automated Lineage and Governance
Modern CDC systems can enrich change events with metadata about who made the change (when user attribution is available), where it originated, and how it propagated across systems. This supports data governance efforts by providing full transparency in data flows.
Warehouse-Centric Compliance with CDC
While traditional compliance workflows focus on source systems like OLTP databases, there's a growing need to enforce compliance policies directly within data warehouses—especially as they evolve into central hubs for analytics, reporting, and operational workflows.
Modern warehouses such as Snowflake, BigQuery, and Apache Iceberg aren't just destinations for data—they are compliance-critical systems where regulatory-sensitive reporting, access control, and audits often occur.
Here’s how CDC strengthens compliance within the warehouse environment:
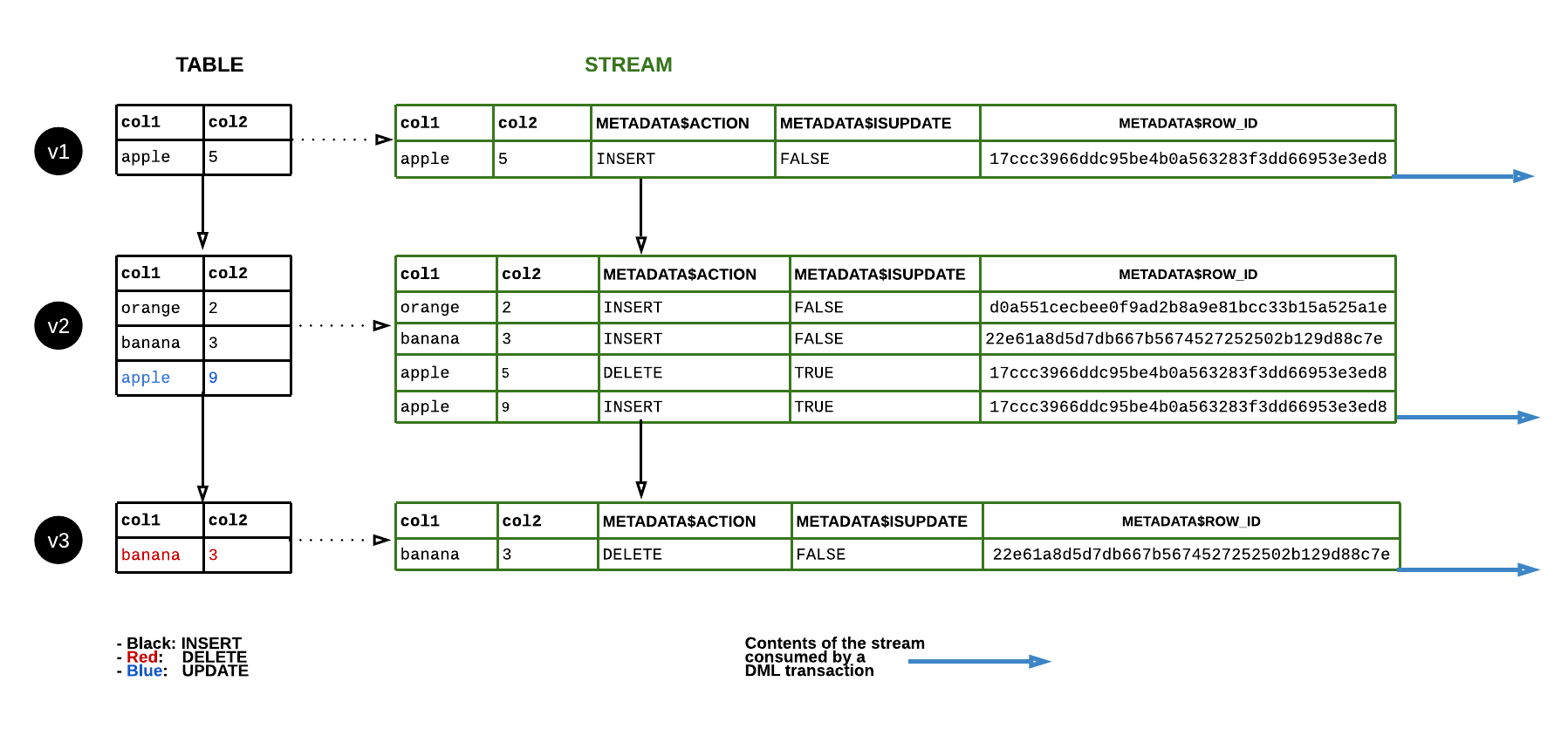
Snowflake: Row-Level Auditing and Access Control
Snowflake is increasingly used for governed analytics in regulated industries like healthcare and finance. By using Snowflake CDC, organizations can:
- Maintain a versioned history of sensitive tables.
- Create secure views or access policies that reflect user permissions on changing data.
- Track who queried or modified data over time using CDC metadata.
- Reconstruct past states for legal discovery or breach investigations.
Estuary Flow supports Snowflake CDC using Streams, allowing you to replicate changes in real time from Snowflake databases and ensure a consistent, queryable historical log for compliance.
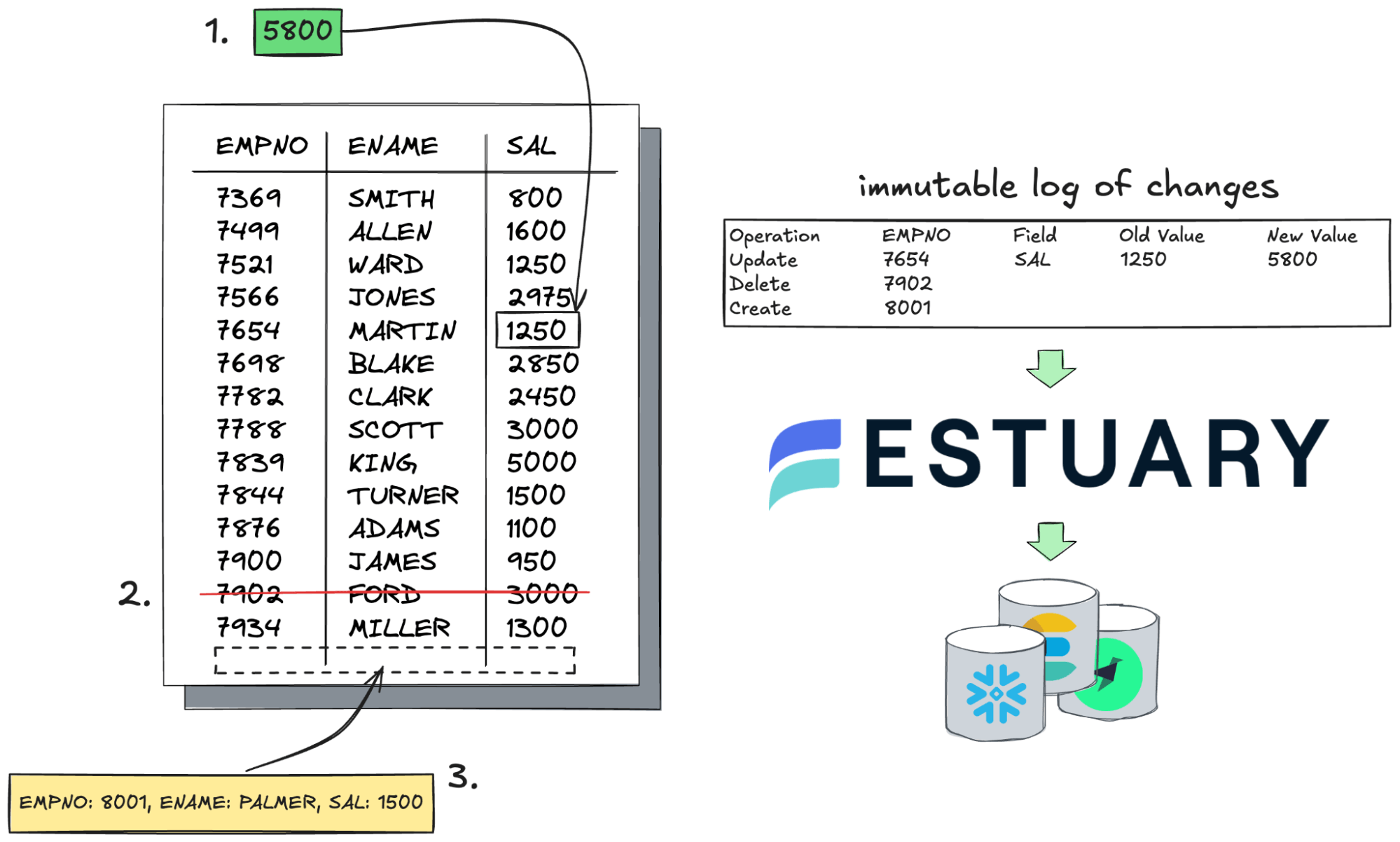
How Estuary Flow Makes CDC for Compliance Easy
Estuary Flow provides a low-latency, schema-aware CDC engine that integrates with a broad array of source systems (like Postgres, MySQL, SQL Server, and even SaaS platforms) and supports real-time materialization to destinations like:
- Cloud object storage (for archiving)
- Analytic databases (for querying audit trails)
- Data warehouses (for historical reporting)
- Apache Iceberg and Delta Lake (for versioned, append-only storage)
Here’s how Estuary Flow enhances CDC for compliance:
- End-to-end encryption to ensure sensitive data is securely transferred and stored.
- Schema evolution support to capture changes in data structure—another compliance requirement.
- Built-in support for historical backfills to ensure your history starts on day one.
- Declarative pipeline definitions so you can codify your compliance strategy in version-controlled configs.
Real-World Example: Financial Data Auditing
A financial services company must retain a complete audit log of all account transactions and modifications. With Estuary Flow, they:
- Capture changes in their PostgreSQL databases using CDC.
- Materialize those changes to Apache Iceberg tables in S3.
- Use versioning and time travel to respond to audits and reconstruct account history.
- Enforce data retention rules via object lifecycle policies.
The result is a resilient, automated compliance pipeline without bolting on complex ETL or building custom scripts.
Conclusion
Change Data Capture isn’t just a performance feature—it’s a compliance enabler. When combined with modern storage and integration platforms like Estuary Flow, CDC helps you:
✅ Meet regulatory mandates
✅ Improve auditability and data governance
✅ Maintain historical visibility without performance tradeoffs
In today’s compliance-driven data landscape, keeping historical changes isn’t a nice-to-have—it’s non-negotiable. CDC is your foundation.
Need help building a compliance-grade CDC pipeline? Talk to our team or get started free with Estuary Flow today.
FAQs
Why are traditional audit trail solutions not enough for regulatory compliance?
Can Change Data Capture be used with data warehouses like Snowflake, BigQuery, or Apache Iceberg?

About the author
Dani is a data professional with a rich background in data engineering and real-time data platforms. At Estuary, Daniel focuses on promoting cutting-edge streaming solutions, helping to bridge the gap between technical innovation and developer adoption. With deep expertise in cloud-native and streaming technologies, Dani has successfully supported startups and enterprises in building robust data solutions.