How Bring Your Own Cloud is solving the impossible equation of enterprise data: SaaS simplicity + on-premises control + real-time performance.
The enterprise data integration landscape has reached an inflection point. Organizations are drowning in the complexity of hybrid environments while simultaneously demanding real-time insights, ironclad security, and cost optimization. Traditional solutions force an uncomfortable choice: accept the limitations of rigid on-premises systems or surrender control to multi-tenant SaaS platforms.
Bring Your Own Cloud (BYOC) is here to save the day. An architectural paradigm that's not just another deployment option, but a fundamental reimagining of how enterprise data integration should work.
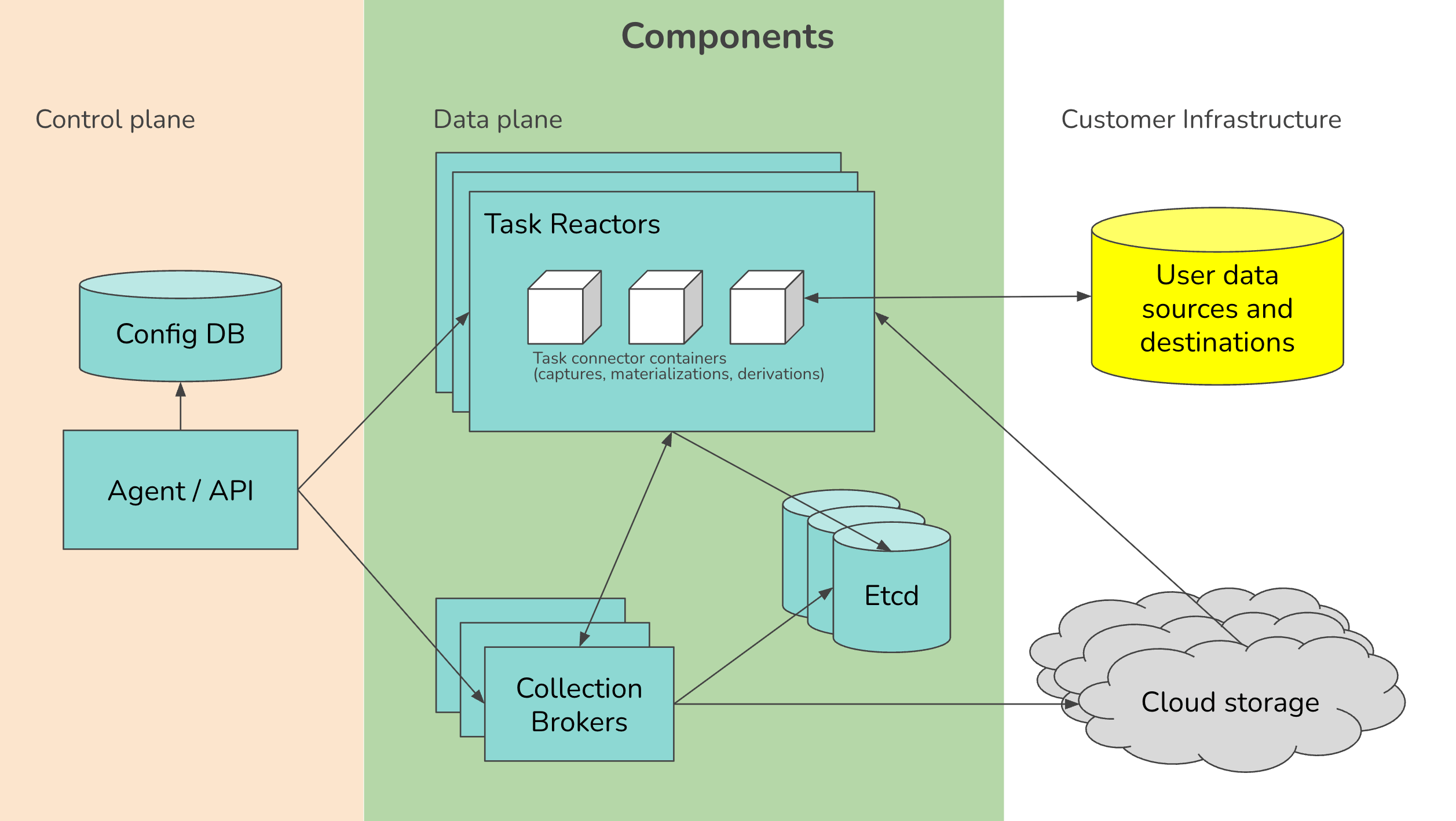
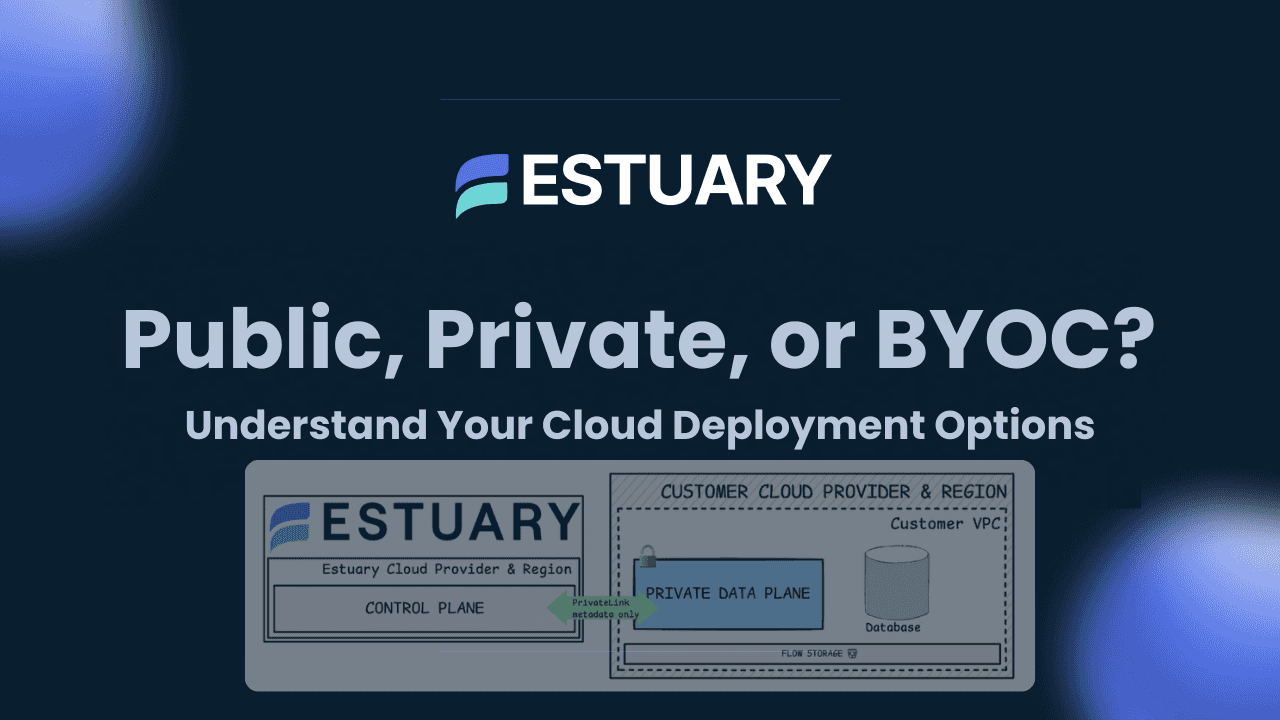
The Technical Foundation: Control Plane vs. Data Plane Architecture
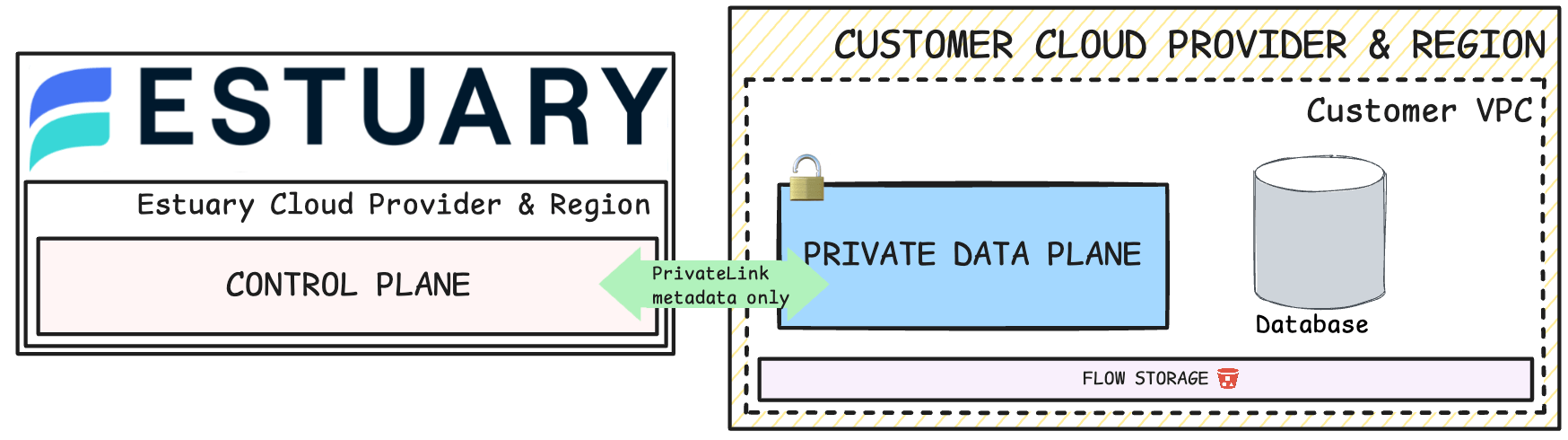
BYOC's power lies in its elegant separation of concerns through a dual-plane architecture that solves the core tension between managed services and data sovereignty.
Control Plane: The Brain in the Cloud
The control plane remains vendor-managed, handling orchestration, monitoring, configuration management, and software updates. This plane operates as a lightweight coordination layer, sending instructions and receiving telemetry through encrypted channels. Think of it as an orchestra conductor directing the performance without touching the instruments.
Data Plane: The Muscle in Your Cloud
The data plane deploys entirely within your cloud environment your VPC, region, and security perimeter. This is where the actual data processing happens: ingestion, transformation, streaming, and storage. Every byte of sensitive data remains under your direct control and is processed by compute resources you own and govern.
This separation enables something previously impossible: you get the operational simplicity of a managed service while maintaining the data locality and security posture of a self-hosted solution.
Learn more: Control Plane vs. Data Plane
Solving Hybrid Cloud's Networking Nightmare
Enterprise networking in hybrid environments is notoriously complex. Firewalls, VPC isolation, private subnets, and air-gapped systems create a maze of connectivity challenges that traditional cloud integration tools simply cannot navigate.
Consider a typical scenario: A financial services company needs to stream real-time transaction data from an on-premises core banking system to a cloud data warehouse for fraud detection. Traditional SaaS integration requires:
- Opening firewall ports for inbound traffic
- Exposing internal systems to the internet
- Routing sensitive data through third-party infrastructure
- Managing complex VPN or direct connect configurations
With BYOC, the integration engine runs inside your network perimeter. Your on-premises connectors communicate locally within your trusted network, while cloud-native integrations operate within your VPC. No firewall exceptions. No data exposure. No complex routing.
Private Connectivity Patterns
BYOC architectures leverage cloud-native private connectivity:
- AWS PrivateLink Integration: The control plane communicates with your data plane through private endpoints, ensuring management traffic never traverses the public internet.
- VPC Peering for Multi-Region: For organizations with global footprints, BYOC enables private connectivity between regions while maintaining data residency requirements.
- Hub-and-Spoke Topologies: Large enterprises can deploy multiple BYOC instances across different business units while maintaining centralized governance through the control plane.
Real-Time Streaming: Where BYOC Truly Shines
Modern enterprises don't just need data integration they need real-time data integration. The rise of operational analytics, fraud detection systems, and AI/ML pipelines has made sub-second data latency imperative for business.
BYOC's local data processing eliminates the network hops and egress delays that plague traditional cloud integration:
Latency Optimization
- Proximity Processing: Data plane co-location with sources minimizes network traversal
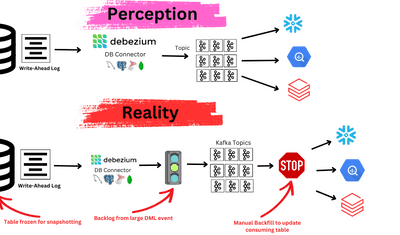
- Local CDC: Change data capture operates at wire speed within your network
- Streaming Architecture: Purpose-built for continuous data flow rather than batch processing
Real-World Performance Impact
A media company streaming clickstream data for real-time personalization saw latency drop from 2-3 seconds (with traditional SaaS integration) to sub-200ms with BYOC deployment. The difference? Their data plane processed events locally before streaming to their cloud analytics platform, eliminating multiple network hops and third-party infrastructure delays.
The Economics of Data Sovereignty
BYOC delivers compelling cost advantages that extend beyond simple price comparisons:
Eliminating Egress Fees
Cloud egress charges can be devastating for data-intensive operations. With BYOC, data movement within your cloud environment incurs no egress fees, only standard intra-cloud transfer costs. For organizations moving terabytes daily, this alone can justify the architectural shift.
Infrastructure Optimization
BYOC lets you leverage existing cloud commitments, reserved instances, and negotiated rates. Instead of paying vendor markups on compute and storage, you utilize your infrastructure agreements.
Predictable Scaling
Resource scaling happens within your cloud account using your governance and budgeting controls. No surprise bills from third-party data processing charges.
Security Architecture: Zero-Trust by Design
BYOC aligns naturally with zero-trust security principles by eliminating the need to trust external infrastructure with your sensitive data.
Threat Surface Reduction
In traditional SaaS integration, your data exists in multiple locations: source, the integration platform, and destination systems. Each area represents potential attack vectors. BYOC collapses this into two parts: your sources and destinations, both under your security control.
Identity and Access Management
Your existing IAM policies, service accounts, and access controls govern the data plane, no need to manage separate identity systems or trust external authentication mechanisms.
Audit and Compliance
Complete visibility into data processing through your existing monitoring and logging infrastructure. Every data transformation, every access event, and every security policy enforcement happens within your auditable environment.
The Regulatory Compliance Advantage
For regulated industries, BYOC isn't just convenient, it's often necessary.
Data Residency Guarantees
Deploy BYOC instances in specific regions to meet local data protection laws. A multinational bank can ensure EU customer data never leaves EU regions while maintaining global data integration capabilities.
Audit Trail Ownership
Compliance auditors can verify data handling practices through your existing governance frameworks. No need to audit third-party infrastructure or trust external compliance certifications.
Industry-Specific Requirements
HIPAA, PCI-DSS, SOX, and other regulatory frameworks often require organizations to control data processing infrastructure directly. BYOC enables cloud-native data integration while meeting these stringent requirements.
Implementation Patterns and Best Practices
Successful BYOC deployments follow established architectural patterns:
Resource Provisioning
Modern BYOC platforms provide infrastructure such as code templates (Terraform, CloudFormation) for consistent, repeatable deployments. This eliminates manual configuration errors and enables version-controlled infrastructure changes.
Monitoring Integration
Data plane metrics and logs integrate with your existing observability stack. Using Datadog, New Relic, or cloud-native monitoring, BYOC telemetry flows through your standard operational workflows.
Disaster Recovery Planning
BYOC instances can leverage your existing backup and disaster recovery procedures. Cross-region replication, automated failover, and point-in-time recovery become extensions of your current infrastructure resilience strategies.
When BYOC Makes Strategic Sense
BYOC isn't universally superior; it's specifically powerful for enterprises with particular characteristics:
- Heavy Regulatory Burden: Organizations in finance, healthcare, government, and critical infrastructure benefit most from the advantages of compliance.
- Significant Data Volumes: Companies processing terabytes daily see immediate cost benefits from eliminating egress fees and vend;or compute markups.
- Complex Security Requirements: Enterprises with zero-trust architectures, air-gapped systems, or extreme security policies find that BYOC aligns with existing security frameworks.
- Mature Cloud Operations: Organizations with established cloud infrastructure, experienced DevOps teams, and existing governance frameworks can maximize BYOC's potential.
The Strategic Imperative: Why BYOC Represents the Future
BYOC isn't just solving today's problems, it's positioning enterprises for tomorrow's challenges:
Multi-Cloud Strategy Enablement
As organizations adopt multi-cloud strategies, BYOC provides consistent data integration capabilities across AWS, Azure, and GCP without vendor lock-in to specific cloud platforms.
AI/ML Pipeline Integration
Modern AI/ML workloads require massive data movement and transformation. BYOC enables these pipelines to operate at cloud scale while maintaining the data locality needed for performance and compliance.
Edge Computing Preparation
As compute moves closer to data sources, BYOC's distributed architecture pattern extends naturally to edge environments, enabling consistent data integration from edge to cloud.
Conclusion: The Architecture of Trust
BYOC represents more than a deployment model; it's a statement of architectural philosophy. It says enterprises shouldn't have to choose between innovation and control, cloud capabilities and data sovereignty, operational simplicity and security rigor.
The most successful organizations of the next decade will be those that can harness cloud-scale data processing while maintaining the security, compliance, and cost control that enterprise success demands. BYOC makes this possible today.
As the enterprise data landscape evolves, BYOC stands as proof that the best solutions don't force compromises; they eliminate the need to compromise at all.
FAQs
How does BYOC improve security and compliance for enterprise data?
Why is BYOC ideal for hybrid and multi-cloud strategies?

About the author
Dani is a data professional with a rich background in data engineering and real-time data platforms. At Estuary, Daniel focuses on promoting cutting-edge streaming solutions, helping to bridge the gap between technical innovation and developer adoption. With deep expertise in cloud-native and streaming technologies, Dani has successfully supported startups and enterprises in building robust data solutions.