Security is one of the most critical and often underestimated factors when choosing a data platform. Whether you're moving data in real time, processing large batch workloads, or powering analytics pipelines across regions, your platform must protect sensitive information at every layer.
For enterprises in regulated industries or those scaling rapidly in the cloud, security isn’t just about encryption or firewalls. It’s about how the platform is architected, how it enforces compliance, and whether it offers the deployment flexibility needed to meet both internal governance and external regulatory standards.
This article outlines five key criteria that organizations should use to evaluate the security of any modern data platform, covering everything from infrastructure design and network isolation to access control and certifications.
Along the way, we’ll highlight how Estuary Flow, a cloud-native platform for both real-time and batch data integration, addresses each of these areas through its zero-trust architecture, flexible deployment models, and enterprise-grade compliance.
1. Regulatory Compliance and Certifications
When evaluating a data platform, one of the first questions any enterprise should ask is: “Can this platform help us meet our regulatory obligations?” Whether you're subject to HIPAA, GDPR, SOC 2, or industry-specific mandates, compliance is more than just a legal requirement — it's a measure of trust, maturity, and operational readiness.
What to Look For
- Independent third-party certifications, such as SOC 2 Type II
- Industry-specific frameworks, such as HIPAA for healthcare or GDPR for international data handling
- Clear documentation of security controls, access policies, and audit capabilities
- The ability to demonstrate compliance in both shared and customer-owned infrastructure
How Estuary Flow Delivers
Estuary Flow has been rigorously tested and certified to support regulated and high-trust environments:
- SOC 2 Type II Certified: Estuary has achieved full SOC 2 Type II certification with no exceptions, demonstrating consistent adherence to stringent operational and security controls.
- HIPAA Compliant: Estuary Flow is certified for handling Protected Health Information (PHI), enabling secure data movement in healthcare and life sciences applications.
- GDPR, CCPA, CPRA Compliant: Estuary complies with global data privacy regulations, ensuring user rights are respected and data usage remains transparent.
These certifications reflect not just policy adherence but a deep integration of compliance into Estuary’s architecture and processes, making it easier for your organization to meet its own audit and regulatory requirements with confidence.
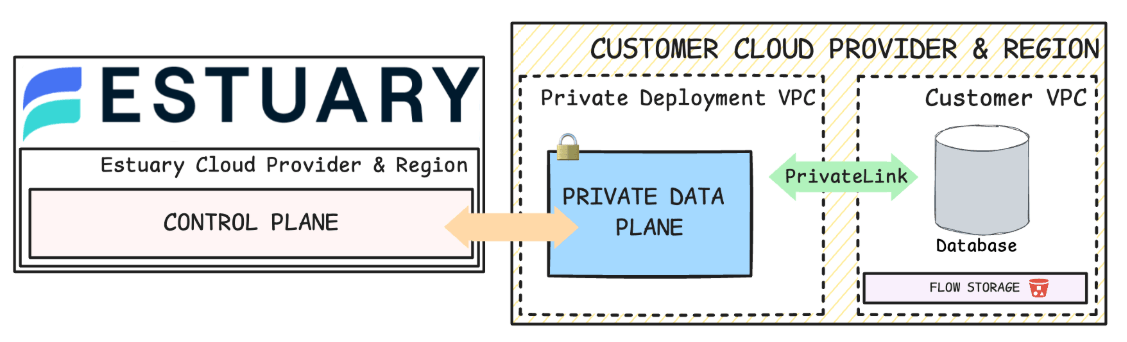
2. Architecture: Control vs. Data Plane Separation
A secure data platform isn’t just about encryption or access controls — it’s about how the architecture fundamentally limits risk. One of the most important architectural principles in secure systems is the separation of the control plane and data plane.
This design allows organizations to manage configurations, orchestration, and monitoring from a centralized control layer, while keeping actual data movement isolated within controlled infrastructure. It reduces the attack surface, enables regional enforcement of data policies, and supports stricter network segmentation.
What to Look For
- Clear separation between management operations (control plane) and data processing (data plane)
- Minimal privilege principles — the control plane should not have access to customer data
- Support for isolated data planes in customer-owned environments
How Estuary Flow Delivers
Estuary Flow is architected from the ground up with this separation in mind:
- The control plane, managed by Estuary, handles orchestration, monitoring, and task configuration.
- The data plane, where data capture, transformation, and materialization occur, can be deployed in Estuary’s cloud or the customer’s own cloud (Private or BYOC deployments).
- In Private Deployments, data remains entirely within the customer’s VPC — Estuary does not access or transmit your data across its infrastructure.
- The separation allows secure multi-region execution, fine-grained access control, and supports hybrid cloud architectures without sacrificing governance.
This architecture not only improves performance and flexibility, it enforces a security boundary that protects customer data by default.
3. Deployment Flexibility and Data Sovereignty
Security doesn’t stop at encryption — it’s also about where your data lives and how much control you have over the infrastructure that processes it. For enterprises with data residency requirements, internal security policies, or regulatory constraints, the ability to choose how and where a platform is deployed is critical.
A secure data platform should allow you to operate in public, private, or fully self-managed (BYOC) environments, without sacrificing features or operational control.
What to Look For
- Multiple deployment models: public cloud, private VPC, and self-hosted options
- Full control over networking, identity, and compute in private environments
- Support for data residency enforcement across regions or jurisdictions
- Zero egress models to reduce risk and cost
How Estuary Flow Delivers
Estuary Flow offers three distinct deployment models to meet varying security and sovereignty needs:
- Public Deployment: A fully managed option hosted by Estuary, ideal for teams without strict residency constraints.
- Private Deployment: Run Estuary’s data plane in your own cloud infrastructure (e.g., AWS, GCP) while retaining the SaaS control plane. Data stays within your network — Estuary never accesses it directly.
- BYOC (Bring Your Own Cloud): Deploy the entire platform — both control and data planes in your own cloud account for maximum control and isolation.
Estuary’s Private and BYOC options support regional data plane isolation, making it easier to comply with GDPR, HIPAA, and internal data governance policies. They also eliminate egress costs and reduce latency by keeping traffic local to your infrastructure.
4. Infrastructure Hardening and Zero Trust Network Model
Security isn't just about external threats — it's also about minimizing internal risk. A platform’s infrastructure must be designed for resilience, immutability, and proactive threat prevention, not just response. The best data platforms adopt zero trust principles, where no service or network is inherently trusted, even internal ones.
What to Look For
- Immutable infrastructure: Systems should be rebuilt, not patched in-place
- OS-level hardening: Kernel modules, mount options, and services should be locked down
- Zero trust networking: Enforce mutual TLS, identity verification, and scoped tokens
- Isolated workload execution: Minimize lateral movement between components
How Estuary Flow Delivers
Estuary applies a deep security-first approach at the infrastructure level:
- Immutable Infrastructure: Estuary uses tools like Pulumi and Ansible to rebuild entire data plane instances on each update, ensuring the latest security patches without configuration drift.
- OS Hardening: Each node runs hardened Ubuntu 22.04 with:
- Disabled insecure kernel modules (e.g., CRAMFS, USB, DCCP)
- Secured partitions (/var, /tmp) with strict mount options
- Disabled unneeded services (FTP, HTTP, Samba) to minimize attack surface
- Zero Trust Networking:
- All communications use TLS, including internal traffic
- Mutual TLS (mTLS) between internal services, with per-data-plane certificate authorities
- Scoped JSON Web Tokens (JWTs) signed per data plane for secure cross-component access
This hardened and zero-trust approach minimizes lateral risk, enforces identity at every layer, and significantly reduces exposure to both external and internal threats.
5. Auditability and Access Controls
Even the most secure systems must be auditable and explainable, especially in enterprise and regulated environments. It’s not enough to protect data; platforms must also provide detailed records of who accessed what, when, and why. The ability to enforce fine-grained access and generate a clear audit trail is essential for internal compliance, external audits, and incident response.
What to Look For
- Centralized access control mechanisms with Role-Based Access Control (RBAC)
- Token-based authentication with expiration and scope limitations
- Full visibility into access logs and authorization decisions
- Support for cross-environment access governance (e.g., across regions or VPCs)
How Estuary Flow Delivers
Estuary Flow provides robust access control and full auditability through a centralized, token-based access model:
- Role-Based Access Control (RBAC): Manage resource-level permissions within and across teams. Tasks and collections can be securely shared or isolated across data planes.
- Scoped, Time-Limited Access Tokens: When a task in one data plane requires access to another, the control plane issues time-bound JWTs only after RBAC checks pass, ensuring least-privilege, traceable access.
- Centralized Authorization + Logging: The control plane logs every access request and token issuance, creating a comprehensive audit trail available for compliance reviews.
- Seamless Inter-Data Plane Access: Estuary’s internal systems (e.g., billing and monitoring) are built using the same secure APIs and token flow customers use — a model of transparent, internally validated access governance.
Estuary’s approach ensures organizations can meet internal audit requirements, respond to security incidents, and maintain accountability — all without introducing operational friction.
Conclusion
Security in the modern data stack is not a feature — it’s a foundation. As organizations integrate more systems, adopt hybrid cloud strategies, and navigate increasingly complex regulatory environments, they need data platforms that go beyond surface-level safeguards.
Evaluating a platform across these five critical dimensions — compliance, architecture, deployment flexibility, infrastructure hardening, and auditability — ensures you select a solution that’s built for long-term resilience and trust.
Estuary Flow embodies these principles by design. Whether you're building real-time pipelines, batch ETL jobs, or hybrid architectures, Estuary provides the tools and deployment models to meet your security and compliance requirements without compromise.
Ready to Evaluate Secure Data Movement?
Estuary Flow is trusted by enterprises to move and transform data securely, in real time or batch, across public, private, and BYOC deployments.
→ Start Building for Free
→ Contact Our Team to discuss your security and compliance needs
FAQs
Why is deployment flexibility important for data security?
How does Estuary Flow ensure secure data movement?
Is Estuary Flow suitable for regulated industries like healthcare or finance?

About the author
With over 15 years in data engineering, a seasoned expert in driving growth for early-stage data companies, focusing on strategies that attract customers and users. Extensive writing provides insights to help companies scale efficiently and effectively in an evolving data landscape.