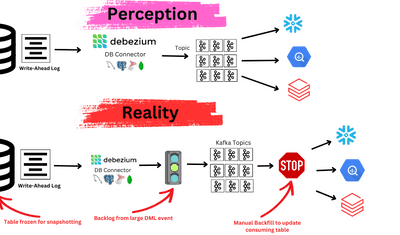
Accurate and reliable information is a key component of organizational functioning. Such information fuels informed decision-making, streamlining operations, and delivering remarkable customer experiences.
Yet, Gartner reports that “every year, poor data quality costs organizations an average of $12.9 million.” Without proper data integrity, which is the assurance that your data is accurate, consistent, and trustworthy, the outcomes would be costly mistakes and poor decision-making. This highlights the critical need for your organization to prioritize data integrity initiatives and maximize the value of data assets.
Maintaining data integrity ensures operational efficiency, builds trust among stakeholders, and supports regulatory compliance.
In this article, you will look into the importance of data integrity and the measures you can implement to achieve it.
What is Data Integrity?
Data integrity refers to the consistency, accuracy, and reliability of data throughout its lifecycle. It ensures that the data you are working with is correct, complete, and unaltered from its original state.
The term data integrity can be seen as both a state and a process. As a state, it defines a dataset that is both valid and reliable; as a process, it describes measures that ensure data accuracy and reliability. Data integrity is crucial for informed decision-making; analytical conclusions can be misleading if the data is compromised or unreliable.
Types of Data Integrity
Understanding the types of data integrity is essential to ensure the accuracy, consistency, and reliability of data within any system.
Data integrity can be mainly classified into physical and logical integrity. Let’s look into the details of these types:
Physical Data Integrity
Physical data integrity ensures that data remains uncorrupted and accessible while stored in physical systems (e.g., hard drives, servers) and during retrieval. It focuses on preventing data loss or damage due to factors such as power outages, storage wear, hardware failures, or cyberattacks.
You can develop recovery plans, protect hardware from damage or wear, and use redundant storage systems to maintain physical integrity.
Logical Data Integrity
Logical data integrity involves sustaining the accuracy and consistency of data while being used in different ways through relational databases. It relies on rules and constraints to prevent inconsistencies or errors.
Logical data integrity can be categorized into four types:
1. Domain Logical Integrity
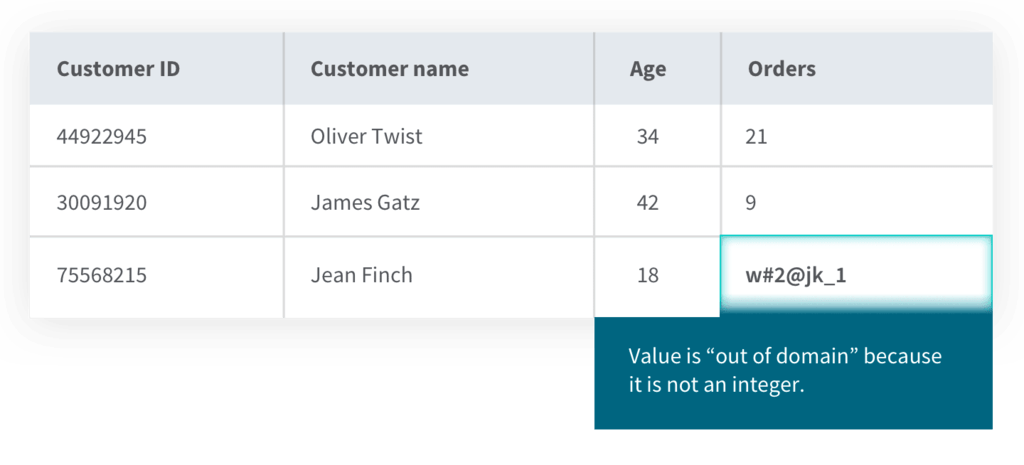
A domain is a set of valid values that a database column is permitted to contain. Domain integrity encompasses rules and procedures restricting the type, format, and volume of data recorded in a database. It helps ensure that all values within your database columns are within a defined set of permissible values.
2. Entity Logical Integrity
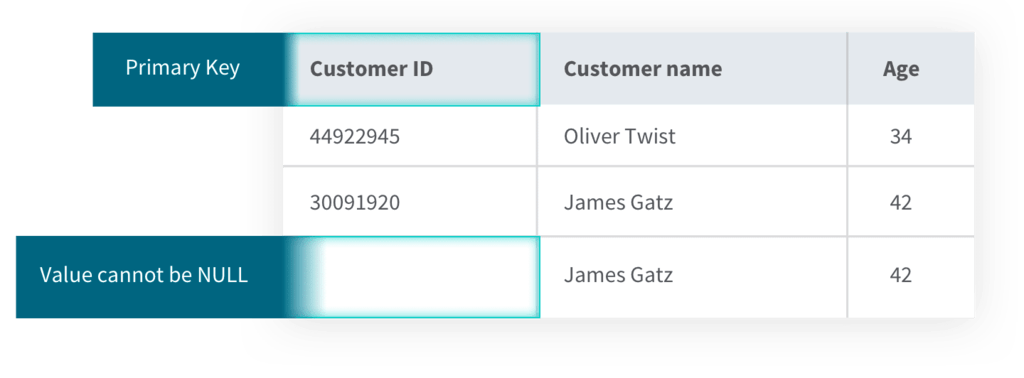
Entity integrity ensures that every row within a database table is unique and has a non-null value, preventing issues like duplicate records that could lead to data corruption. You can enforce entity integrity using primary keys and UNIQUE constraints in a database table.
For example, in a customer table, each record should have a unique customer ID, which helps distinguish one customer from another and prevents any duplicate values.
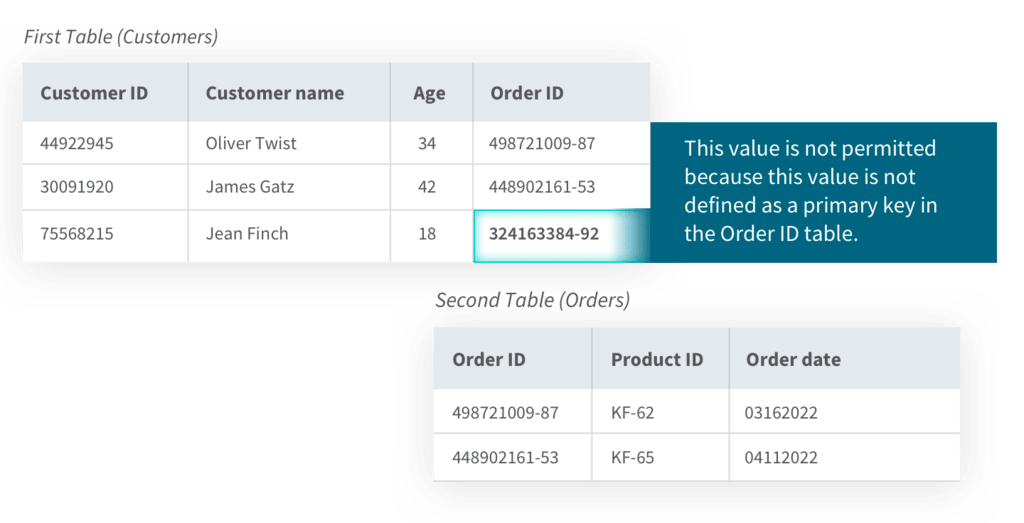
3. Referential Integrity
Referential integrity (RI) is a data quality concept that enables you to maintain the consistency of the relationships between data in a database. You can apply the concept of RI using foreign key constraints, relationship cardinality rules, and relationship models. The relationship models help define and outline regulations governing how different data entities relate to each other.
4. User-Defined Integrity
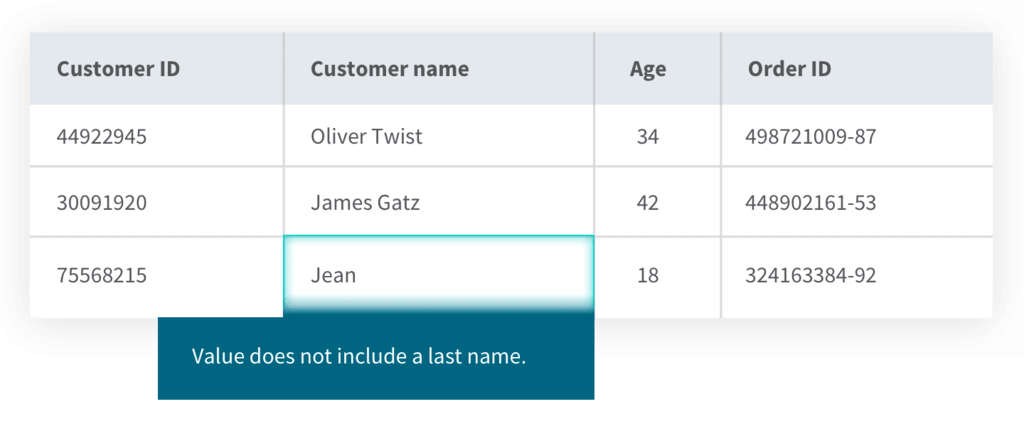
User-defined integrity allows you to set and enforce custom integrity rules specific to your business requirements. You can define custom business rules and constraints that trigger automatically when predefined events occur.
For example, you might require that every customer record include both first and last names. If you attempt to save a record without this information, the database will reject the action or prompt you to provide missing data.
Why Data Integrity Matters
Accurate analytics depend on the integrity of the data. If the data you use is compromised in any way, your analysis will be less reliable. Maintaining data integrity saves time, effort, and money by preventing decisions based on incorrect or incomplete data.
Here are some points highlighting the importance of data integrity:
- Correctness: Data integrity ensures that data is accurately represented and helps prevent errors that can lead to incorrect analysis or poor decisions.
- Completeness: Maintaining data integrity ensures that datasets are comprehensive and contain all the necessary information, avoiding gaps that can mislead decision-making.
- Accuracy: Data integrity guarantees that data is precise and truthful, supporting accurate insights.
Common Causes of Data Integrity Issues
When data integrity is compromised, the consequences can range from the minor loss of a pixel in an image to major incorrect medical decisions. Sometimes, even a single missing piece of data can make your entire data useless.
There are different causes for compromised data integrity, including:
Data Replication
Data replication is the process of storing the same data in multiple locations. If you replicate data at various times and places, the data may be out of sync. This happens because updates made in one location might not be immediately reflected in others, leading to discrepancies and inconsistent datasets.
Data Transfer
Data transfer is the process of copying data from one storage device to another or between systems. Interruptions during the data transfer can result in incomplete datasets, which might impact critical operations, such as analysis, that rely on complete and consistent data.
Evolving Cyber Threats
Cyberattacks are increasingly becoming sophisticated, with the development of innovative malware and highly personalized phishing attacks. These threats make it harder to protect data and ensure its integrity, as they can introduce unauthorized changes, corruption, or loss of data. To mitigate these risks, an effective IAM architecture is essential, ensuring that only authorized users can access sensitive information.
Risks of Poor Data Integrity
Failing to maintain data integrity can lead to significant challenges, such as:
Operational Inefficiencies
Data integrity issues can result in duplication or inconsistent data within internal systems. If systems have conflicting or outdated information, it can slow down operations, cause delays, or require additional manual work to correct errors. Over time, these inefficiencies can increase operational costs and reduce overall productivity.
Inaccurate Decision Making
Flawed data can lead to poor decision-making in critical areas like budgeting, planning, and strategy. For example, basing a sales forecast on incorrect customer data might result in overestimating or underestimating demand. This can create problems such as stock shortages or excess inventory, disrupting business operations and customer satisfaction.
Data Breaches and Security Risks
Compromised data integrity can result in inconsistencies, errors, and weak security measures. For example, without proper validation, sensitive data might get exposed to unauthorized access, making systems vulnerable to breaches, malware, or other cyberattacks.
Non-Compliance
If your data is incorrect or missing, it can result in non-compliance with regulations such as GDPR (for privacy) or HIPAA (for healthcare). This non-compliance can lead to legal risks, including substantial fines, penalties, or reputational harm.
Reputation Damage
A company’s reputation depends heavily on trust. Data errors or privacy breaches can negatively impact customer and partner confidence. This can attract negative media attention, damage your brand’s credibility, and cause a decline in brand value and loss of business opportunities.
Best Practices for Ensuring Data Integrity
How do you ensure data integrity? The answer is to use a reliable approach that follows best practices, such as the ALCOA framework. It is a recognized set of principles that has five essential characteristics defining high-quality and trustworthy data:
- Attributable: Records who and what performed an activity.
- Legible: Ensures that data is readable throughout its lifecycle.
- Contemporaneous: Involves documenting the activity at the time it occurs.
- Original: Maintains records that are either original or certified first copies.
- Accurate: Reinforces precision to ensure data and records are free from errors.
Here are some best practices to help uphold these principles:
Access Controls
Implementing access control mechanisms helps protect sensitive data from unauthorized access. For example, with a role-based access control (RBAC) framework, you can restrict access to authorized personnel based on their roles and responsibilities.
You can also implement user authentication and permission levels for actions like reading, writing, or deleting data. This protects data authenticity and ensures accountability.
Implement Data Encryption
Encryption involves securing data using a format accessible only with a decryption key. This helps to protect sensitive data both during transmission (with frameworks like SSL/TLS) and at rest (with disk encryption).
Detailed Audit Trails
Maintain detailed logs for all actions performed on data, including creation, modification, and deletion, along with timestamps and user information. These records can help you track changes and ensure that data is attributable and contemporaneous.
Qualities of an ideal audit trail include:
- It should be generated automatically.
- Nobody should be able to tamper with the logs or records.
- Every event should be aligned with the user who made the change.
- Include timestamps for all events to track when they occurred.
Validate Input and Data
Validating data input involves checking it against pre-defined rules and standards to ensure its accuracy and consistency. For example, validation checks can ensure the numerical field contains only numbers, dates are in a specific format, and required fields are not left blank.
Back up Data
To avoid data loss, it’s essential to create regular backups. These backups, or copies of data, are useful in the event of hardware failures, accidental deletions, or cyberattacks. Ensure you store backups securely and test them periodically for recoverability.
Promote Cultural Integrity
Data integrity is not just about taking precautionary measures but creating a work environment that promotes a culture of honesty and responsibility. Encourage team members to be transparent and truthful about the data they handle. When people take ownership of their work and are committed to being honest, it helps keep the organization on track and maintain high standards of accuracy.
Tools and Technologies to Support Data Integrity
There are several tools and technologies designed to support data integrity, each serving a specific purpose in the data management lifecycle. Let’s explore these categories:
Data Governance Tools
Data governance tools help define and document data integrity requirements, standards, and policies using features like metadata, glossaries, and catalogs. These features help to organize and track data across the organization, ensuring consistency.
Some examples of data governance tools include Azure Preview and Collibra Data Governance.
Suggested read: Data Governance: Framework, Principles, & Best Practices
Data Validation Tools
Data validation tools help check the data for consistency, completeness, and accuracy. These tools allow you to identify missing values, duplicates, outliers, or invalid formats. They also facilitate enforcing data standards and rules across data sources and processes.
Examples of data validation tools are Informatica, Talend, and SQL Server Data Quality Services (DQS).
Data Cleansing Tools
Data cleansing tools improve data quality by removing, modifying, or replacing errors, such as typos or inconsistencies. These tools help implement operations like merging, deduplication, and data consolidation to create reliable datasets.
Some examples of data cleansing tools include Trifacta Wrangler and Microsoft Power Query.
Suggested read: What Is Data Cleansing?
Data Profiling Tools
Data profiling tools help you analyze the structure, content, and quality of data. With these tools, you can get a better understanding of the characteristics, patterns, and relationships of the data, including its type, format, length, range, and dependencies.
Examples of data profiling tools include IBM InfoSphere, Oracle Data Quality, and SAS Data Management.
Data Transfer Tools
Data often gets transferred between systems, such as moving from write-optimized storage to a read-optimized query database. As this point of transfer is one of the common areas where issues arise, it pays to carefully consider how you will move data from one system to another.
Data transfer tools, such as ETL platforms or pipeline services, will perform replication for you. A good tool will ensure data integrity by translating source to destination formats and ensure data in the destination system remains up-to-date.
Examples of data transfer tools include Estuary and other ETL, ELT, and CDC tools.
Achieve Comprehensive Data Integrity With Estuary During Integration
Preserving data integrity during the integration process between systems is important, as inconsistencies can compromise analytics and disrupt workflows. Estuary helps maintain the integrity of data at every stage of the ETL process. Its competent features ensure that data remains accurate and reliable.
Here are some mechanisms with which Estuary guarantees data integrity:
- Schema Evolution: Schema evolution allows you to update the entire data flow and reflect the changes made to your data collections. This ensures accurate, up-to-date data capture and delivery from source to destination. As a result, data consistency is maintained throughout the integration process.
- Compliance with Governance Frameworks: Estuary complies with industry data governance standards, including CCPA, GDPR, HIPAA, and SOC2 Type II. This compliance with regulatory frameworks ensures that your data is handled securely and privacy and integrity are maintained.
- Flexible Deployments: Estuary offers deployment options to suit your infrastructure needs. It offers three deployment options: Public, Private, and BYOC. This flexibility provides control over data, enabling consistent and reliable data management, regardless of where it resides.
Conclusion
Data integrity is key to ensuring smooth operations within any organization. When your data is accurate and consistent, it enables processes to run efficiently, minimizes errors, and supports more reliable decision-making. By maintaining high data integrity, you can enhance productivity, improve customer experiences, and set the path for sustainable long-term growth.
Looking for an efficient and secure way to integrate your data between multiple platforms? Try Estuary for your varied integration needs. All it takes is a few minutes to set up your data pipeline with guaranteed data integrity.
FAQs
What are the five principles of data integrity?
The five principles of data integrity are attributable, legible, contemporaneous, original, and accurate. By implementing these principles across your organization’s data management process, you can ensure the accuracy and correctness of data.
What is the role of data classification in maintaining data integrity?
Data classification helps maintain data integrity by ensuring the data is properly classified based on its sensitivity and importance. There are four common levels of classification: public, internal-only, confidential, and restricted. You can optimize data classification to prevent unauthorized access and data breaches

About the author
Dani is a data professional with a rich background in data engineering and real-time data platforms. At Estuary, Daniel focuses on promoting cutting-edge streaming solutions, helping to bridge the gap between technical innovation and developer adoption. With deep expertise in cloud-native and streaming technologies, Dani has successfully supported startups and enterprises in building robust data solutions.