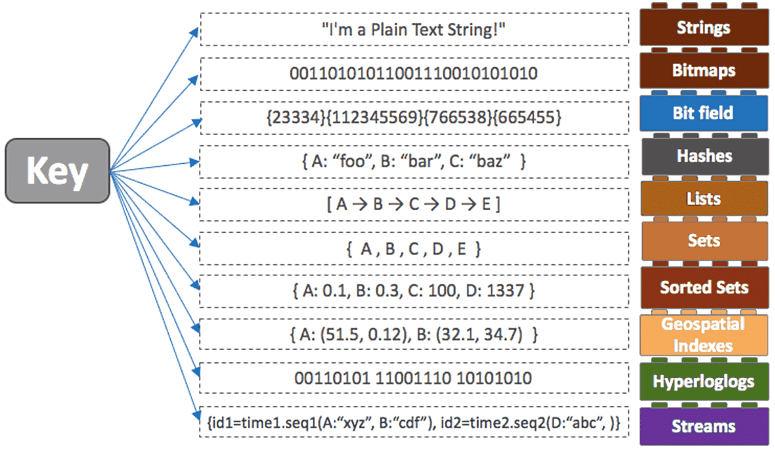
Redis data types go beyond the typical notions of databases. These data types, combined with an advanced set of commands and data structures, are designed for performance, flexibility, and utility. They provide the framework for efficient data storage and retrieval and let developers model and optimize data interactions.
Just to give you a sense of how popular Redis is, over 27,773 companies use it to power their real-time applications. While Redis has taken the world by storm, it's not a smooth ride for everyone. Behind the scenes of its wide adoption, there are challenges. We are talking about tricky things like synchronization, data persistence, and making sure things run smoothly as you scale up.
To help you with this ordeal, we’ll break down these daunting walls of confusion and help you understand how choosing the right Redis data type and pairing it with strong data pipelines can unlock the full potential of Redis’ powerful data structures in modern applications.
What Is Redis?
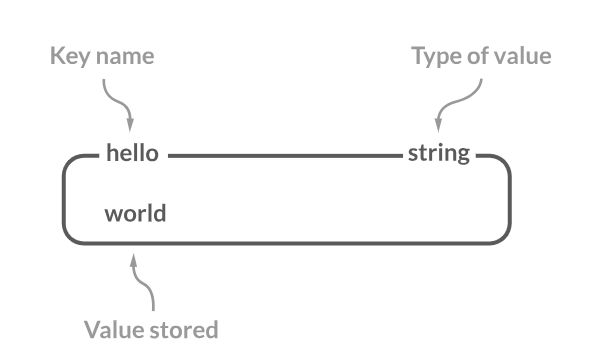
Redis is an open-source, in-memory key-value database that is very fast, flexible, and full-featured. The data is stored in RAM rather than disk, providing faster access and throughput. Redis stores data as key-value pairs. The key acts as an identifier and the value can be a string, list, set, hash, or other Redis data type.
This key-value approach makes Redis a versatile data structure server that can handle use cases beyond a simple database. Some of the key benefits of Redis are:
- Speed: It is incredibly fast with sub-millisecond latencies for most operations. This makes it ideal for real-time applications.
- Rich feature set: It provides built-in replication, Lua scripting, transactions, pub/sub messaging, and many other advanced features.
- Versatility: It can be used as a database, cache, message broker, and more. Its flexible data structures power different modern applications.
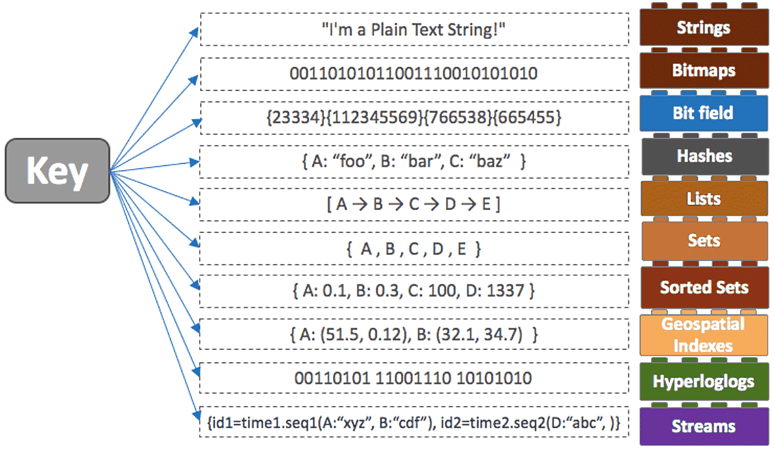
7 Major Redis Data Types You Need to Know
Redis has a large range of data structures optimized for different uses. Knowing and selecting the appropriate Redis data type helps you build high-performance systems tailored to your application’s needs.
Let’s look at the most commonly used abstract data types in Redis.
String
In Redis, strings are known to be ‘binary safe’. A Redis string represents any data, irrespective of its type. This could be textual data, like a user’s name or email, or binary data like an image or a serialized object. String values can actually store values of different types which makes the string data type quite versatile.
A Redis string can store up to 512 MB of data, and this maximum limit applies individually to both the key and its associated value. Because of these constraints in size and the in-memory nature of Redis, operations on strings are typically fast.
Commands & Their Usage
1. The SET command is used to associate a key with a string value. If the key already exists, this command will overwrite the old value.
plaintextredis-cli SET username “john_doe”Here, the key “username” is set to have the value “john_doe”.
2. The GET command fetches the value associated with a specified key.
plaintextredis-cli GET usernameFor our earlier example, this would return the value “john_doe” associated with the key “username”.
3. The DEL command deletes the value associated with a key.
plaintextredis-cli DEL usernameThis would delete the “john_doe” value set.
Practical Application
Redis strings are versatile and are commonly used for caching web pages or other expensive database queries.
For instance, you can cache the HTML of a user’s profile page in Redis after the first time it’s generated. When another user visits the same profile, you can swiftly fetch the cached HTML from Redis rather than re-rendering the entire page, thus improving speed and reducing server load.
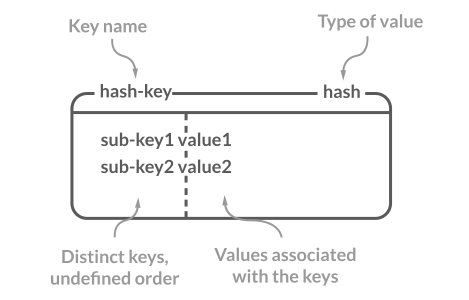
Hash
In Redis Hash, a string key is mapped to a string value. This collection of key-value pairs is particularly suited for representing objects. For example, you can represent a user object where each field corresponds to a user attribute, like name, email, or age.
These fields, or keys, are unique within each hash. However, the same field can exist in multiple separate hashes. Also, it’s not possible to use other complex data structures like Sets, Lists, or additional Hashes as values.
Commands & Their Usage
1. The HSET command sets a field (or key) to a particular value within a hash. If the field already exists in the hash, its value gets overwritten.
plaintextredis-cli HSET user:1 name “Alice”Here, within the hash represented by “user:1”, we are setting the “name” field to have the value “Alice”.
2. The HGET command fetches the value associated with a specified field in a hash.
plaintextredis-cli HGET user:1 nameUsing the previous example, this command fetches the value “Alice” associated with the field “name” in the hash represented by “user:1”.
3. The HGETALL command fetches all fields and values in a hash.
plaintextredis-cli HGETALL myhashThis retrieves all fields and values from the hash stored in “myhash”.
Practical Application
Redis Hashes are perfect when you have a large number of objects with the same set of fields. This could be user profiles where each user has attributes like name, email, age, and address. With hashes, you can store each user’s attributes in a structured manner and quickly access or modify individual attributes without affecting others.
List
Redis Lists are ordered collections of strings. They are unique since they are implemented as linked lists. This means that operations at the beginning or the end of the list, like adding or removing elements, are executed in constant time which makes them extremely fast. This data type is particularly useful when you want to maintain an order of elements like a timeline of activities or a log of events.
Commands & Their Usage
1. The LPUSH command inserts a new value at the start of the list. If the key does not exist, a new list is created.
plaintextredis-cli LPUSH fruits “apple”In this command, “apple” is added to the beginning of the list represented by the key “fruits”.
2. The RPOP command removes and returns the last value of the list. This is useful when you’re using a list as a stack and want to retrieve the most recent addition.
plaintextredis-cli RPOP fruitsThis command will remove and return the value “apple” from the list “fruits”.
Practical Application
Lists are versatile and can be used in different scenarios. One common use is for implementing queues. Jobs or tasks can be “pushed” onto a list and workers can then “pop” tasks from the list for processing. This means that tasks are processed in the order they are received
Another example is a social media timeline where recent activities are added to the start of the list and users view activities from the start to the end of the list.
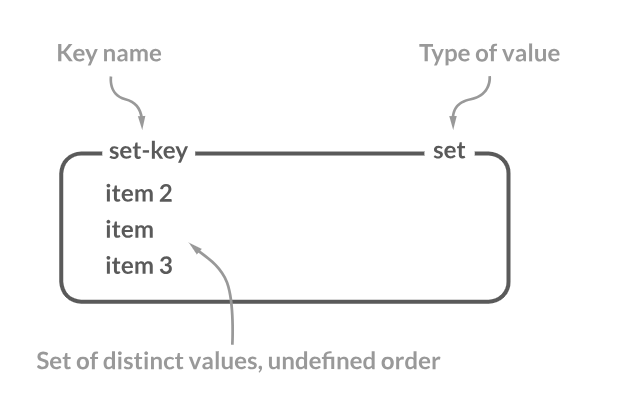
Set
A Set in Redis is an unordered collection of strings where each string is unique. This means there are no duplicate entries in a Redis set. This unique property of sets makes them useful when you need to track a collection of items without any repetition, like tracking user tags, IP addresses, or even user IDs for unique visitors.
Commands & Their Usage
1. The SADD command is used to add one or multiple values to a set. If a value already exists in the set, it will not be added again, maintaining the uniqueness of values in the set.
plaintextredis-cli SADD tags “music”In this command, the value “music” is added to the set represented by the key “tags”. If “music” already exists in this set, the set remains unchanged.
2. The SMEMBERS command retrieves all the members or values of a set.
plaintextredis-cli SMEMBERS tagsUsing the previous command as a reference, this command fetches all the members of the set “tags”. In our case, it will return “music” among potentially other tags.
3. The SISMEMBER command checks if a value is a member of a set.
plaintextredis-cli SISMEMBER myset "value"This checks if “value” exists in the set “myset”.
4. The SREM command removes the specified member from a set.
plaintextredis-cli SREM myset "value"This removes “value" from the set “myset”.
Practical Application
Sets are ideal when you want to avoid repetition. For instance, if you're building a social media platform where users can add tags to a post, you can use a Redis set to store these tags. This means that even if a user tries to add the same tag multiple times, it will only be stored once.
Another application is in analytics where you want to track unique visitors to a website. Each time a user visits, you can add their user ID or IP address to a Redis set. This way, even if the user visits multiple times, they will be counted only once.
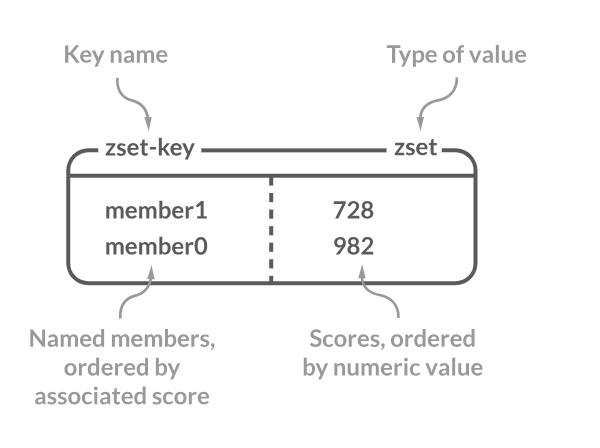
Sorted Sets
Sorted sets, also known as Zsets (Z for “Z-scored”), are a collection of unique members just like sets. However, what sets them apart is the association of each member with a score which is a floating point number.
The members in a Sorted Set are always taken in order by their score which provides a consistent ordering. This structure is especially useful when you need to maintain an order of elements based on a ranking or scoring mechanism like leaderboards in games, page rankings in search results, or even time series data.
Commands & Their Usage
1. The ZADD command adds a member with its score to the sorted set. If the member already exists, its score is updated.
plaintextredis-cli ZADD leaderboard 100 “player1”In this command, the member “player1” is added to the sorted set “leaderboard” with a score of 100. If “player1” already exists, its score will be updated to 100.
2. The ZRANGE command retrieves members of the sorted set within a specified score range.
plaintextredis-cli ZRANGE leaderboard 0 -1This command fetches all members of the sorted set “leaderboard” from the start (0) to the end (-1) in ascending order of their scores.
3. The ZSCORE command returns the score of a specified member in the sorted set.
plaintextredis-cli ZSCORE leaderboard “player1”Based on our previous commands, this will fetch the score of “player1” from the “leaderboard” sorted set, which is 100.
4. The ZRANGEBYSCORE command returns members within a given score range.
plaintextredis-cli ZRANGEBYSCORE myzset 0 100This fetches members from “myzset” that have scores between 0 and 100.
5. The ZREM command removes members from a sorted set.
plaintextredis-cli ZREM myzset "member"This removes “member” from the sorted set “myzset”.
Practical Application
One of the most widespread applications of sorted sets is in gaming leaderboards. As players score points in a game, their scores can be updated in real-time in a Redis-sorted set. This speeds up the retrieval of top players, player rankings, or even players in a specific score range.
Another application is time series data. When you use timestamps as scores, you can store events or logs in chronological order and retrieve events within specific time ranges swiftly. Redis sorted sets provide a balance between the uniqueness of sets and the ordering based on scores.
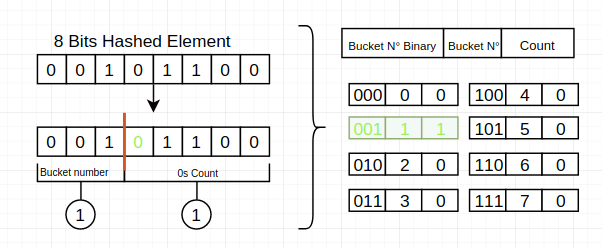
Probabilistic Data Structures
Redis supports a few probabilistic data structures and one of the most notable is HyperLogLog. It is designed to provide approximations rather than exact answers. It can estimate the cardinality (or unique count) of a set with a tiny memory footprint.
HyperLogLog is particularly useful when you want to count unique elements, like the number of unique visitors to a website, but you are willing to trade off a bit of accuracy for major memory savings.
Commands & Their Usage
1. The PFADD command adds an element to the HyperLogLog data structure. If the specified key doesn’t exist, a new HyperLogLog data structure is created.
plaintextredis-cli PFADD visitors "user1"In this command, the element “user1” is added to the HyperLogLog data structure associated with the key “visitors”.
2. The PFCOUNT command returns the approximate cardinality of the elements observed in the HyperLogLog.
plaintextredis-cli PFCOUNT visitorsThis command fetches the approximate number of unique elements in the HyperLogLog data structure associated with the key “visitors”.
3. The PFMERGE command merges multiple HyperLogLog values into a single value.
plaintextredis-cli PFMERGE myhll1 myhll2 myhll3This merges “myhll1”, “myhll2”, and “myhll3” into a single HyperLogLog value.
Practical Application
Imagine you’re running a high-traffic website and want to track the number of unique visitors daily. Using traditional data structures could require significant memory when the number of visitors increases. With HyperLogLog, you can get a reasonably accurate estimate of unique visitors using minimal memory.
Another use case is in big data analytics where datasets are too large to process with exact algorithms. Here, HyperLogLog provides fast, memory-efficient estimates for unique counts.
Advanced Data Types
2 of the advanced data types in Redis are bitmaps and geospatial indexes. Bitmaps are strings where each bit represents a unique value, making them highly space-efficient for certain dataset types. On the other hand, geospatial indexes help store and query geographical data.
Bitmaps are incredibly useful for analytics where you want to track user behavior or presence. While geospatial indexes are used in location-based services, they help perform operations like finding all nearby locations within a certain radius.
Let’s see how Bitmaps work.
Commands & Their Usage
1. The SETBIT command sets or clears a specific bit in the string value associated with a key.
plaintextredis-cli SETBIT user:1:visited 7 1This command sets the bit at offset 7 for the key “user:1:visited” to 1. If the key doesn't exist, a new string is created with the specified bit set.
2. The GETBIT command retrieves the value of a specific bit in the string value associated with a key.
plaintextredis-cli GETBIT user:1:visited 7Based on our previous command, this will fetch the value of the bit at offset 7 for the key “user:1:visited”, which is 1.
3. The BITOP performs bitwise operations between strings.
plaintextredis-cli BITOP AND destkey srckey1 srckey2This performs a bitwise AND operation between “srckey1” and “srckey2”.
4. The BITPOS finds the first bit set to 1 or 0 in a string.
plaintextredis-cli BITPOS mykey 1This finds the first bit set to 1 in “mykey”.
5. The BITCOUNT counts the number of set bits in a string.
plaintextredis-cli BITCOUNT mykeyThis counts the number of set bits (1s) in “mykey”.
Practical Application
Bitmaps are used when space efficiency is crucial. For instance, if you’re building a website and want to track the days a user visited in a month, you can use a bitmap with 31 bits (one for each day). Each bit can be set or cleared based on the user’s visitation pattern.
Supercharge Data Management and Transformation With Estuary Flow
Flow is our ETL tool for effective and efficient data management. It is designed to make data movement and transformation straightforward and reliable, from source to destination. Whether you’re working with traditional databases, modern SaaS applications, or hybrid cloud environments, Estuary Flow helps you in all scenarios.
Let’s look at the key features that make this tool important for your real-time data management needs:
- Scalability: Designed as a distributed system, it easily scales to meet your data volume needs, even handling throughput up to 7 GB/s.
- Transformations: True streaming SQL and JavaScript transformations give you powerful and instantaneous data manipulation capabilities.
- Extensibility: Open protocol design in Estuary Flow lets you add new connectors. This makes it highly adaptable to evolving data ecosystem needs.
- Schema inference: The tool automatically converts unstructured data into a structured format. This simplifies data preparation for analytical or operational use.
- Data capture: Flow specializes in data capture from different sources like databases and SaaS applications, offering a one-stop solution for all your data collection needs.
- Real-time monitoring: Live reporting and monitoring functionalities are built into Estuary Flow which gives you real-time insights into your data flows and operations.
- Operational efficiency: Using low-impact CDC technology, it provides one-time data capture that can be replicated across all your systems, optimizing operational workflows.
- Data consistency: The platform employs exactly-once semantics to guarantee transactional consistency and provide an authentic and reliable snapshot of your data landscape.
- Resilience: With cross-region and data center support, Estuary Flow guarantees operational continuity and ensures that cloud provider downtimes have zero impact on your data workflows.
Conclusion
Redis data types and their corresponding commands form a dynamic toolkit that lets you create efficient and robust applications. Redis steps into the spotlight with roles in caching, real-time analytics, messaging, and more.
This makes it a must-have foundation for modern applications and gives developers the tools to create systems that are not only efficient but also flexible to meet the demands of today’s digital landscape.
Are you looking to gain an edge by building a robust and efficient data pipeline? Try Estuary Flow for free. It easily lets you capture, transform, and deliver data from various sources to power your applications.

About the author
With over 15 years in data engineering, a seasoned expert in driving growth for early-stage data companies, focusing on strategies that attract customers and users. Extensive writing provides insights to help companies scale efficiently and effectively in an evolving data landscape.