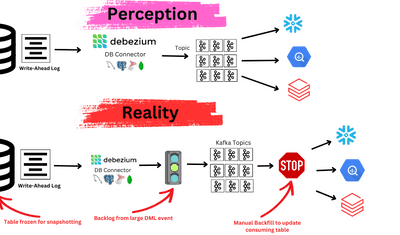
Introduction: Why ACID Transactions Are the Foundation of Reliable Data Systems
When you transfer money from one bank account to another, you expect the debit and credit to both happen correctly. Imagine if the debit occurred but the credit failed because of a system crash. This is where ACID transactions come into play.
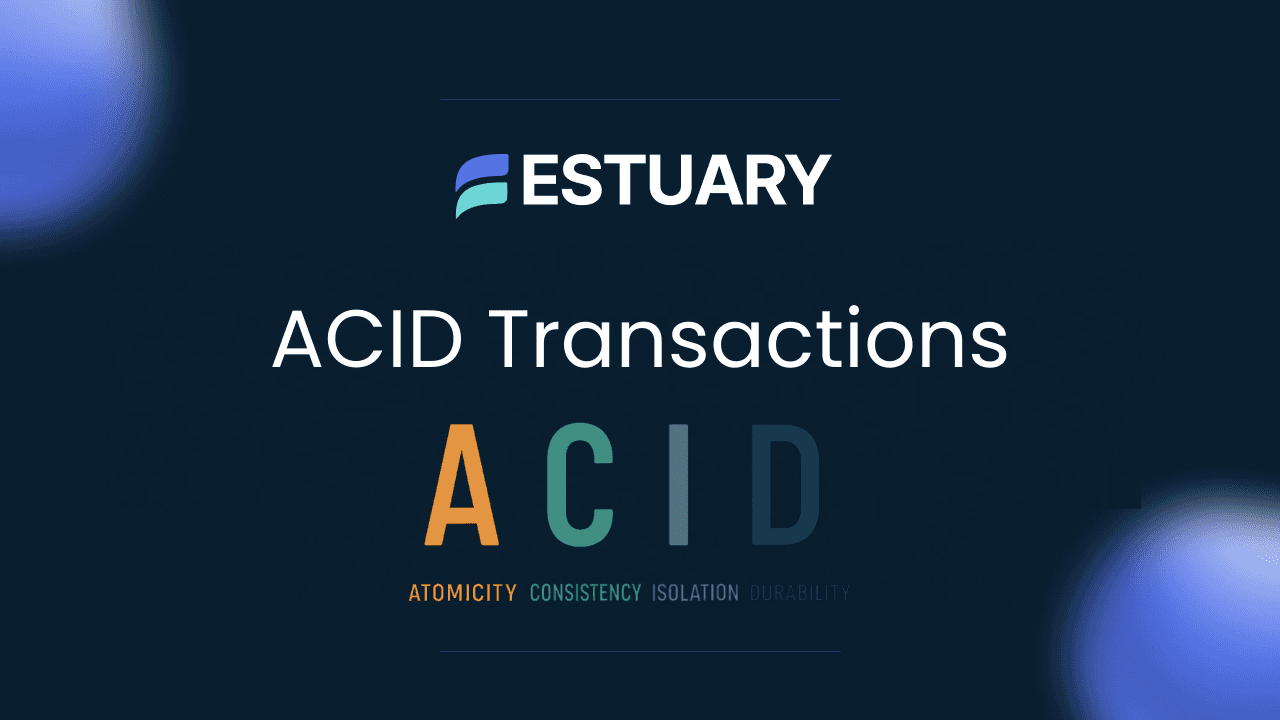
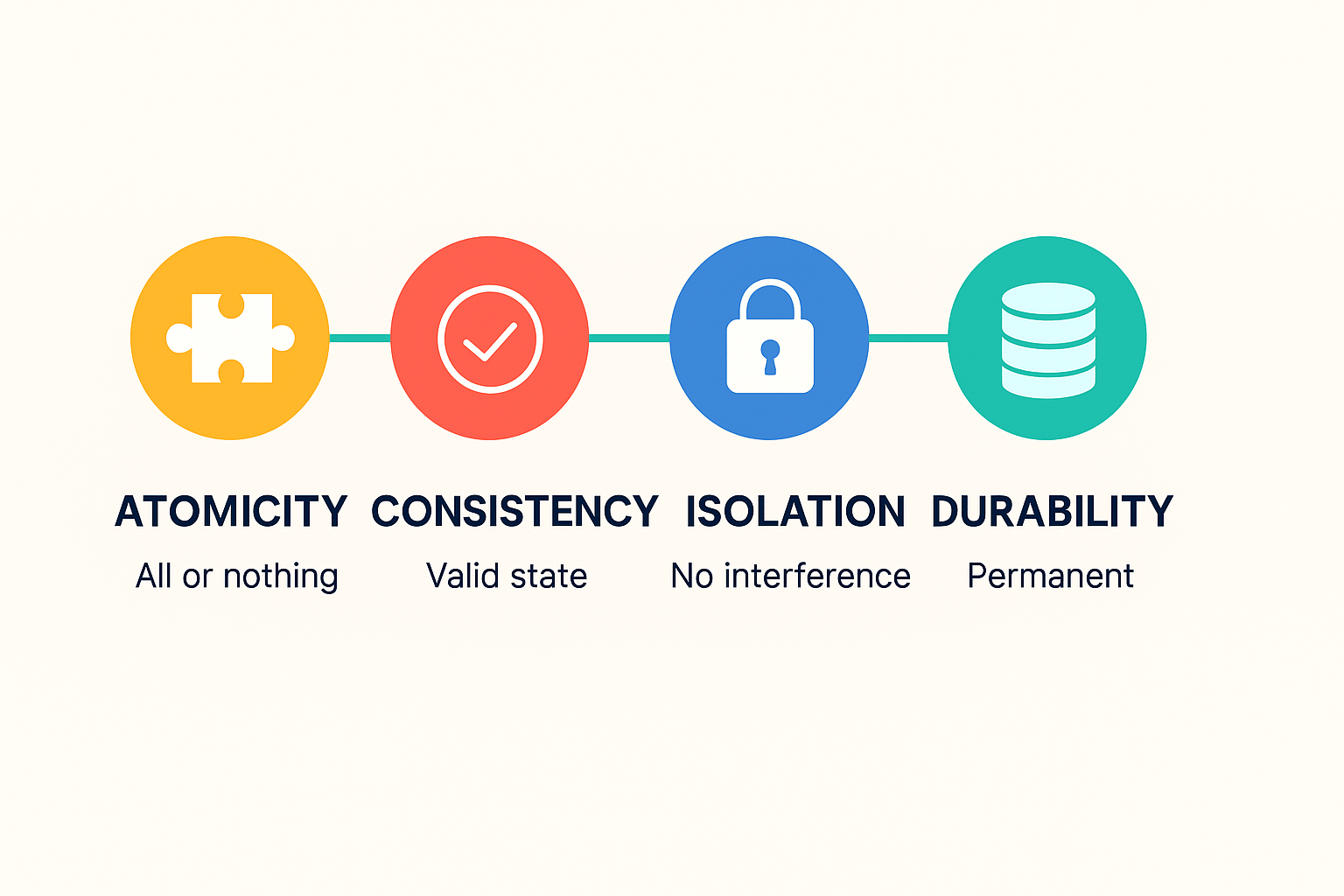
ACID stands for Atomicity, Consistency, Isolation, and Durability. These four properties ensure that a database transaction is processed reliably, even in the face of unexpected errors or failures. They are not just abstract concepts from computer science textbooks. They are the reason you can trust online payments, flight bookings, e-commerce orders, and healthcare systems to work as expected.
In the modern data landscape, ACID principles are not limited to traditional relational databases. They influence how data is moved, processed, and stored in real-time data pipelines, especially when maintaining exactly-once delivery and data consistency across distributed systems.
This article will explain what ACID transactions are, why they are important, how they work in databases like PostgreSQL, MySQL, and MongoDB, and how these principles extend to real-time streaming platforms like Estuary Flow.
The Four Pillars of ACID Transactions
ACID transactions get their name from the four key properties that guarantee reliability in database operations. Understanding each property helps explain why ACID-compliant systems are considered the gold standard for data integrity.
1. Atomicity
Atomicity means that all operations within a single transaction are treated as one indivisible unit. Either every step of the transaction completes successfully, or none of them do.
Example: In a bank transfer from Account A to Account B, both the debit from Account A and the credit to Account B must succeed together. If one step fails, the entire transaction is rolled back, leaving the database unchanged.
In practice: Databases implement atomicity using techniques like transaction logs and rollback mechanisms.
2. Consistency
Consistency ensures that a transaction moves the database from one valid state to another, following all defined rules, constraints, and triggers.
Example: In an e-commerce database, a product’s available quantity should never become negative. Consistency checks prevent invalid data from being written to the database.
In practice: Database constraints, triggers, and referential integrity rules enforce consistency at every transaction commit.
3. Isolation
Isolation ensures that concurrent transactions do not interfere with each other’s results. Multiple users can safely access and update the database at the same time without causing incorrect data states.
Isolation levels in SQL databases include:
- Read Uncommitted
- Read Committed
- Repeatable Read
- Serializable
Example: If two customers try to buy the last item in stock at the same time, isolation ensures that only one transaction succeeds in reserving it.
In practice: Databases use locking mechanisms and multi-version concurrency control (MVCC) to enforce isolation.
4. Durability
Durability guarantees that once a transaction is committed, its results are permanent, even in the event of a system crash or power failure.
Example: If you book a flight online and receive confirmation, the booking remains valid even if the airline’s server crashes an instant later.
In practice: Databases use write-ahead logging (WAL), backups, and replication to maintain durability.
ACID in Practice
ACID is more than just a theoretical concept. Modern database systems use specific mechanisms to enforce each property, making transactions reliable and predictable.
ACID in Relational Databases
Most relational database management systems (RDBMS) such as PostgreSQL, MySQL (InnoDB engine), SQL Server, and Oracle Database are designed to be ACID compliant. They achieve this through a combination of:
- Transaction logs to ensure atomicity and durability
- Constraints and triggers to maintain consistency
- Concurrency control methods such as locking and Multi-Version Concurrency Control (MVCC) to provide isolation
Example in PostgreSQL:
plaintextBEGIN;
UPDATE accounts SET balance = balance - 100 WHERE id = 1;
UPDATE accounts SET balance = balance + 100 WHERE id = 2;
COMMIT;If either update fails, the database will roll back the entire transaction to its previous consistent state.
ACID in NoSQL Databases
Traditionally, many NoSQL systems like MongoDB and Cassandra prioritized scalability and flexibility over strict ACID compliance. However, modern versions have added support for multi-document ACID transactions to handle use cases that require strong consistency.
Example: MongoDB introduced full ACID transactions in version 4.0, allowing operations across multiple collections with commit and rollback support.
Distributed and Cloud Databases
Distributed databases and cloud-based services like Google Spanner, Amazon Aurora, and CockroachDB apply ACID principles across multiple nodes. This often requires complex consensus algorithms like Paxos or Raft to maintain consistency and durability across regions.
ACID vs BASE - The Distributed Systems Trade-Off
While ACID transactions are the foundation of reliability in traditional databases, not every system uses them. In large-scale distributed environments, many databases and data platforms follow a different set of principles known as BASE.
What is BASE?
BASE stands for Basically Available, Soft state, Eventually consistent. It is a design philosophy often used in distributed databases and real-time systems where high availability and scalability are prioritized over strict consistency.
- Basically Available: The system guarantees availability of data, even if some nodes fail.
- Soft State: The system’s state can change over time without input due to asynchronous replication.
- Eventually Consistent: All nodes will converge to the same data state, but not necessarily instantly.
ACID vs BASE
Aspect | ACID | BASE |
| Consistency | Strong, immediate consistency | Eventual consistency |
| Availability | May be sacrificed to maintain strict consistency | High availability is prioritized |
| Use Case | Banking, e-commerce checkout, healthcare records | Social media feeds, IoT event collection, analytics |
| Complexity | Easier to reason about correctness | Requires careful design for handling stale data |
Choosing the Right Model
- Use ACID when data correctness is non-negotiable and each transaction must be fully reliable.
- Use BASE when the system needs to scale horizontally to millions of users and can tolerate slight delays in data synchronization.
Estuary Flow’s Approach
Real-time streaming pipelines often operate in distributed environments, where maintaining full ACID compliance can be challenging. Estuary Flow incorporates ACID-like guarantees through:
- Exactly-once delivery to prevent duplicates and data loss.
- Schema enforcement to maintain consistency across systems.
- Recovery logs to ensure durability even during failures.
This approach blends the reliability of ACID with the scalability of BASE, making it possible to have real-time performance without compromising on data integrity.
Where ACID Principles Matter in Data Pipelines
While ACID transactions are most often discussed in the context of relational databases, the same principles are essential in data pipelines, especially those moving data between multiple systems in real time.
1. Finance
Financial systems depend on atomicity and consistency to prevent errors in monetary transactions. A single missing record in a fraud detection pipeline could lead to false negatives and major financial losses.
Example: A credit card processing pipeline that uses change data capture (CDC) from PostgreSQL to a fraud detection engine must ensure no partial or duplicate transactions.
2. E-commerce
ACID principles prevent inventory mismatches during high-traffic sales events. If multiple systems update product counts without isolation, overselling can occur.
Example: Streaming order events from MySQL to a fulfillment system requires exactly-once delivery to keep inventory accurate.
3. Healthcare
Durability and consistency are crucial for patient data. Lost or corrupted data can have serious consequences.
Example: Synchronizing patient records from an operational database to a reporting system must guarantee that updates are complete and permanent.
4. Logistics
Shipment tracking and warehouse inventory systems rely on transaction integrity to ensure accurate, up-to-the-minute data.
Example: Real-time syncing of delivery status from a SQL Server system to a customer-facing portal needs both durability and isolation to avoid showing wrong shipment details.
Pros and Cons of ACID
ACID transactions are often considered the gold standard for reliability in database systems, but like any design choice, they come with trade-offs. Understanding these advantages and disadvantages helps in deciding when strict ACID compliance is the right fit.
Advantages of ACID Transactions
- High Data Integrity
Transactions either complete fully or not at all, preventing partial updates that can lead to corrupted data. - Error Recovery
Rollback mechanisms allow systems to revert to a consistent state after errors or failures. - Predictable Behavior
Developers and analysts can trust that data reflects a correct and complete state, simplifying reasoning about system behavior. - Concurrency Safety
Isolation ensures that multiple users or processes can work with the database simultaneously without creating conflicts.
Disadvantages of ACID Transactions
- Performance Overhead
Enforcing isolation and durability can slow down systems under heavy load. - Reduced Scalability
In distributed systems, strict consistency can limit the ability to scale horizontally. - Complex Implementation
Managing locks, logs, and rollback mechanisms adds complexity to system design. - Resource Consumption
Write-ahead logging and replication for durability require additional storage and processing.
How Estuary Flow Brings ACID-Like Reliability to Streaming Data
Traditional ACID transactions are typically confined to a single database. In modern architectures, however, data often needs to flow between multiple systems — transactional databases, cloud warehouses, analytics engines, and real-time applications. Ensuring ACID-like reliability across these distributed environments is challenging.
Estuary Flow addresses this challenge by embedding key ACID principles into its real-time data movement framework.
1. Exactly-Once Delivery
Flow ensures that each record is processed a single time, preventing both duplicates and missing data. This is crucial when syncing critical data between systems such as PostgreSQL and Snowflake.
2. Schema Enforcement
Flow validates data against a defined schema before writing it to a destination. This preserves consistency, ensuring that all downstream systems receive data in a correct and expected format.
3. Transactional Materializations
Materializations in Flow commit data atomically. Either all changes from a batch are applied together or none are applied, mirroring the atomicity of traditional ACID transactions.
4. Durable Storage and Recovery
Flow uses recovery logs to maintain durability across failures. If a connection is interrupted, processing resumes from the exact point it left off, without reprocessing data incorrectly.
5. Isolation in Concurrent Processing
Flow handles parallel tasks without cross-interference. This keeps concurrent data syncs from corrupting or overwriting each other’s changes, providing a form of isolation across distributed pipelines.
By combining these capabilities, Estuary Flow extends ACID-like reliability beyond single databases to the complex, multi-system pipelines that modern businesses rely on. This makes it possible to achieve both real-time performance and data integrity at scale.
Conclusion
ACID transactions remain one of the most important concepts in database design. They guarantee that every transaction is atomic, consistent, isolated, and durable, which is critical for maintaining trust in systems that handle sensitive or high-value data. From banking and healthcare to e-commerce and logistics, ACID principles ensure that data stays correct even in the face of unexpected failures.
In today’s distributed and real-time environments, applying ACID across multiple systems is not always straightforward. That is where solutions like Estuary Flow come in — extending ACID-like guarantees to streaming data pipelines. By combining exactly-once delivery, schema enforcement, transactional materializations, and durable recovery, Flow bridges the gap between traditional database reliability and modern real-time performance.
Whether you are designing a transactional database system or building a streaming pipeline, understanding ACID principles will help you make the right architectural choices. And when you need to maintain this level of reliability at scale across diverse systems, Estuary Flow offers a practical way to get there.
FAQs
What is an example of an ACID transaction?
What are the benefits of ACID transactions?
How do ACID transactions maintain data integrity?

About the author
Team Estuary is a group of engineers, product experts, and data strategists building the future of real-time and batch data integration. We write to share technical insights, industry trends, and practical guides.